- Scheme is a multi-vector attack that involves a hierarchy of administrators, workers, and callers, who organize their activities through a Telegram bot.
- Malicious actors will create a bait ad on a legitimate marketplace, usually offering a high-value technology item.
- Actors attempt to move conversation to a messaging application like WhatsApp.
- By bypassing any communication protection that marketplace provides, actors get the victim to pay through fraudulent sites.
On January 14, 2021, threat hunting company Group-IB published a report on a new scam scheme that they named “Classiscam.” They reported that there are 40 or more groups currently running this multi-vector attack across Russia and Europe. The scheme involves a hierarchy of administrators, workers, and callers, who organize their activities through a Telegram bot. The scam itself targets customers of online marketplaces with a combination of baits, messages, and fraudulent sites to steal a victim’s money.
While there seem to be a couple of variations, here is the core of how this multi-vector attack works: The malicious actors will create a bait ad on a legitimate marketplace, usually offering a high-value technology item with a significant discount. The actor will then send a request to the Telegram bot, which will provide the actor with scam materials for the ad (including a fraudulent payment page). When a potential victim contacts the actor through the marketplace, the actor will attempt to move the conversation to a messaging application like WhatsApp. There, the actor will provide the victim with a link to the fraudulent payment page.
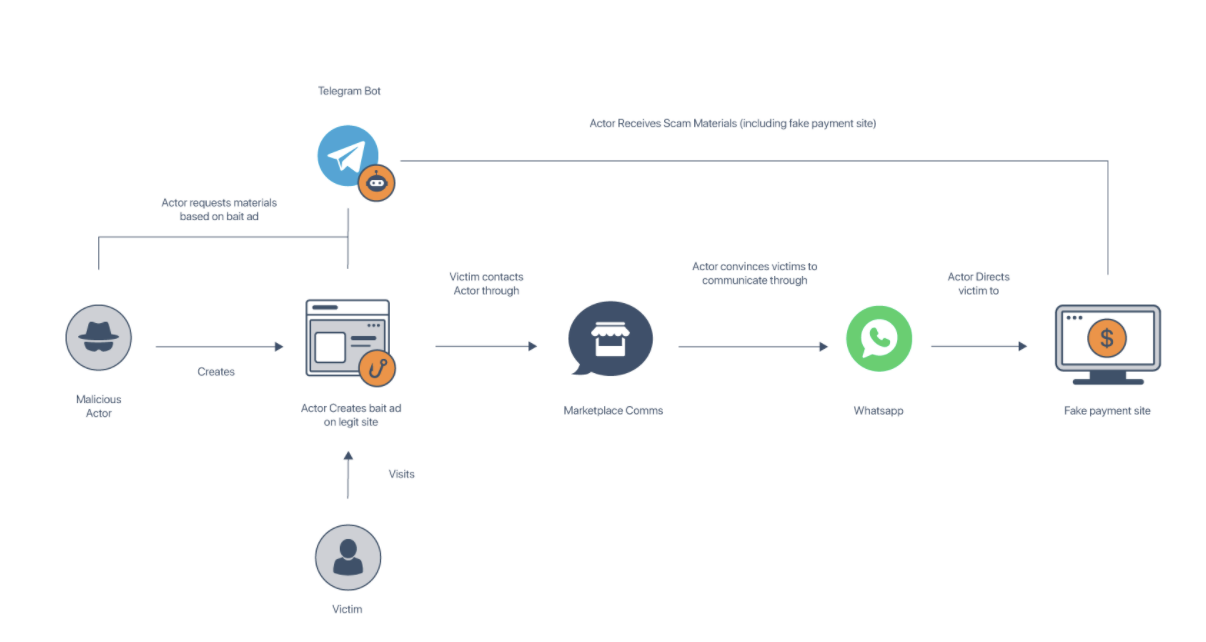
By directing victims to WhatsApp, the actors can bypass any communication protection that the marketplace might otherwise be able to provide (such as flagging or blocking suspicious links). If they get the victim to pay through the fraudulent site, they avoid any payment protection the marketplace may have offered (such as refund on items not delivered).
The SafeGuard Cyber solution can help prevent multi-vector attacks like these from affecting you and your employees by protecting your messaging apps. SafeGuard Cyber takes the same level of protection and security traditionally found in email security solutions (such as identifying, flagging, and blocking suspicious language, links, and attachments) and applies it to your messaging applications. In this example, SafeGuard Cyber would have examined the WhatsApp message’s link and flagged or quarantined the message before it could reach the potential victim. That would have immediately alerted the potential victim to the suspicious nature of the messages and cut out a key link in the chain of events of the attacker’s plan.
SafeGuard Cyber can also be adopted in TotalPrivacy mode, which allows security teams to review risk events without exposing the content of an individual’s communications. If you are interested in learning more about the security solution at SafeGuard Cyber and how you can protect yourself and your employees from tactics used by multi-vector attacks and schemes like Classiscam, you can contact us and request a demo today.
Case Study: Learn how a Global pharma leader deploys
automated security and compliance solution for WhatsApp.

.jpg)