Today, nearly half of all business communication takes place in channels outside of email. Contextual Analysis can help security teams quickly identify and correlate risks across their entire communications environment, from collaboration platforms to email and even personal messaging apps.
Begin your transformation to secure and compliant communication. Share your information so we can connect.

Download PDF
Executive Summary
Today, nearly half of all business communication takes place in channels outside of email, spanning enterprise channels like Slack, Teams, and Zoom, as well as personal channels like LinkedIn, WhatsApp, Signal, and Telegram. With both types of channels accessible across managed and unmanaged endpoints, the complexity of the modern communication ecosystem increases. While most business communications are benign, some involve the exchange of proprietary information, such as financial data or intellectual property.
"Communications are a blind spot for most organizations."
— Director of IT, Security, and Compliance Healthcare Company
Threat actors are increasingly aware that security teams often have limited visibility into emerging communication channels, leading to a significant expansion of the attack surface. These adversaries are exploiting this gap by deploying sophisticated social engineering techniques and language-based attacks. Utilizing tactics like impersonation, deception, urgency, and semantic manipulation, they are adept at convincing targets to deviate from normal behavior. This approach is not just prevalent but alarmingly effective; studies indicate that cybercriminals employ social engineering in a vast majority of attacks. These methods have been central to some of the most damaging cyber incidents in recent times, including high-profile breaches at companies like Uber, Twilio, Nvidia, Okta, Microsoft, Axie Infinity, and MGM.
As the landscape of business communication continues to grow and evolve, encompassing a wide array of cloud channels, CISOs and SOC teams are recognizing the urgent need for enhanced visibility into the context and intent of communications. This is crucial to prevent sophisticated attacks from escalating into significant business communication compromises (BCC).
In this paper, we explore how Contextual AI, a key feature of the FirstSight platform, empowers organizations to gain insight into the context and intent of communications. This capability is instrumental in detecting BCC attacks earlier in the kill chain by identifying leading threat indicators such as social engineering, unusual communication exchanges, and abnormal user behavior.

Contextual AI in Cybersecurity
Contextual AI – the process of breaking down a digital conversation in order to better understand it – is a modern, highly efficient, and powerful toolset for defenders. It gives security teams visibility into the flow of messages in cloud communication channels so they can more easily and quickly locate, identify and neutralize threats. While most security tools are designed to detect traditional attack indicators, such as malicious links or attachments, Contextual AI is fundamentally different: it’s designed to help teams quickly examine the language in today’s complex communications ecosystem for more efficient threat identification.
SafeGuard Cyber deploys advanced Contextual AI capabilities powered by the platform’s Natural Language Understanding (NLU) engine to extract meaningful insight from unstructured language. By analyzing the content and context of a message, including language-based lexical features, spelling features and topical features, it provides security teams with clear insight into the human element behind cyberthreats, including:
– Who is talking?
– What are they talking about?
– What are they saying about those subjects?
– What sentiments are being expressed?
Based on these results, security teams can determine if a conversation is benign or if something suspicious is taking place. Contextual AI helps teams determine if a conversation is part of a plan to obtain sensitive information or escalate privileges, or if it has the hallmarks of a social engineering attack using elements such as urgency or undue persuasion. By evaluating the WHY and the HOW of communications, Contextual AI makes it possible for security teams to detect language-based attacks that can be leading indicators of business compromise.
The human element plays a crucial role in 74% of security breaches. This underscores the central importance of the human factor in the realm of cybersecurity, with a notable increase in social engineering attacks. The report highlights a significant rise in pretexting incidents, which now account for more than 50% of all social engineering attacks, and emphasizes the growing prevalence of Business Email Compromise (BEC) attacks. These findings demonstrate the evolving nature of cyber threats and the continued exploitation of human vulnerabilities in security breaches.
2023 Verizon Data Breach Investigations Report
businesses worldwide are targeted by phishing scams daily.
of data breaches have been found to have social engineering components associated with them.
the number of phishing websites as malware sites are existing.
of attacks by cybercriminals use social engineering.
of companies worldwide were victims of phishing in 2020.
was the cost per compromised record on average.
Recent Social Engineering Attacks Highlight Security Gaps
Some of the most devastating social engineering attacks in 2022 and 2023 were conducted against Nvidia, Okta, and Microsoft by the Lapsus$ group, and MGM by the AlphV and Scattered Spider. Using communication channels like WhatsApp, Slack, and Teams, they gained access to hundreds of gigabytes of Nvidia’s proprietary data, including information about chips that the company is developing. In addition, Lapsus$ claims to have stolen the credentials of thousands of Nvidia Employees.
In January, cybercriminals stole 20 GB of credit card information from guests and employees of Marriott International in the UK. In this breach, the threat actors used social engineering attacks to lure an employee into providing access to their employee’s computer.
In March, the Blockchain company Ronin lost almost $615 million worth of cryptocurrency through an attack on Ronin’s network blockchain bridge. Using a fake LinkedIn job offer to phish an employee, the attackers stole 173,600 Ethereum cryptocurrency tokens and 25.5 million in USD Coin in just two transactions. In response to these attacks, Ronin’s parent company, Sky Mavis, said it is looking to become a “zero-trust organization."
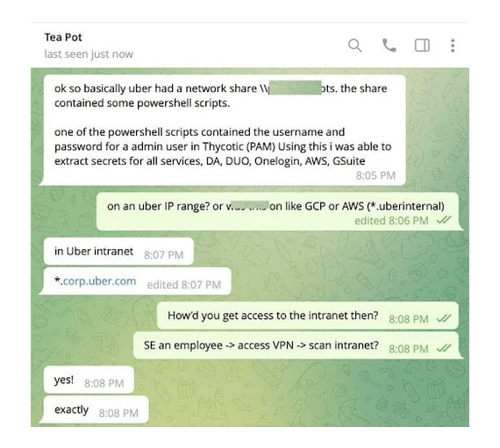
During September, a 16-year-old cybercriminal took advantage of a loophole in Uber’s security system, to crack into the system. Impersonating Uber’s IT team, the attacker sent multiple and continuous MFA push notifications to a contractor across SMS and WhatsApp. In this case, the seeming urgent nature of the notifications eventually wore down the employee who eventually logged in and had their credentials promptly stolen.
Weeks later, the same cybercriminal compromised an employee at Rockstar Games, then used those credentials to impersonate the employee, breaching the company's Slack instance to steal intellectual property and leak it publicly.

The Changing Nature of Work
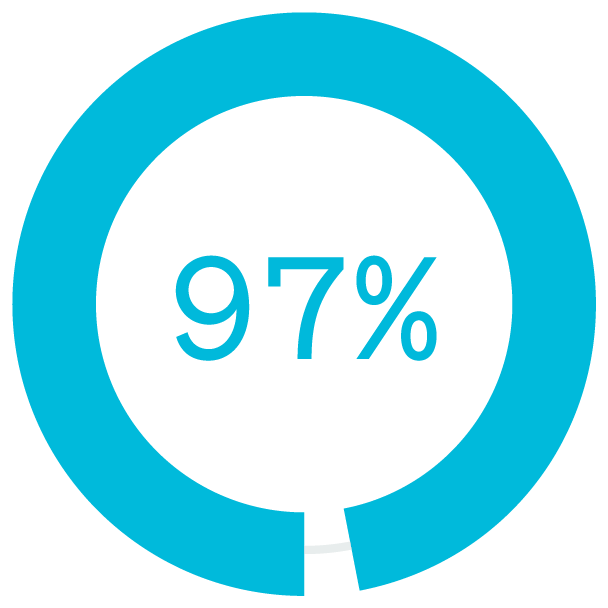
of North American office workers worked from home more than one day per week
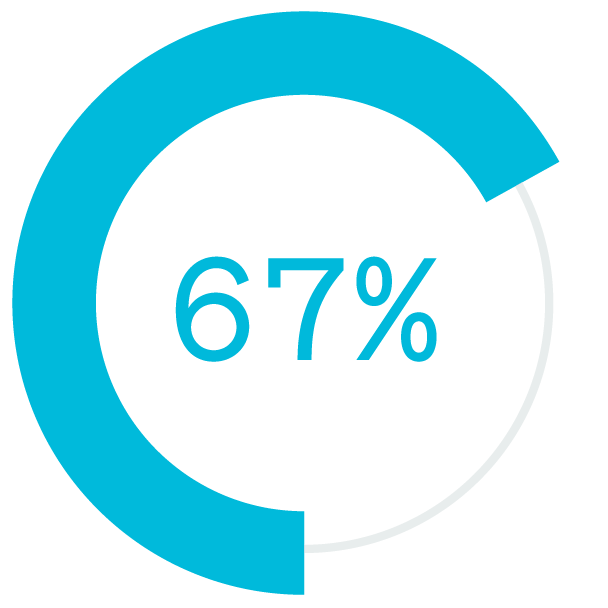
had not worked remotely prior to COVID-19
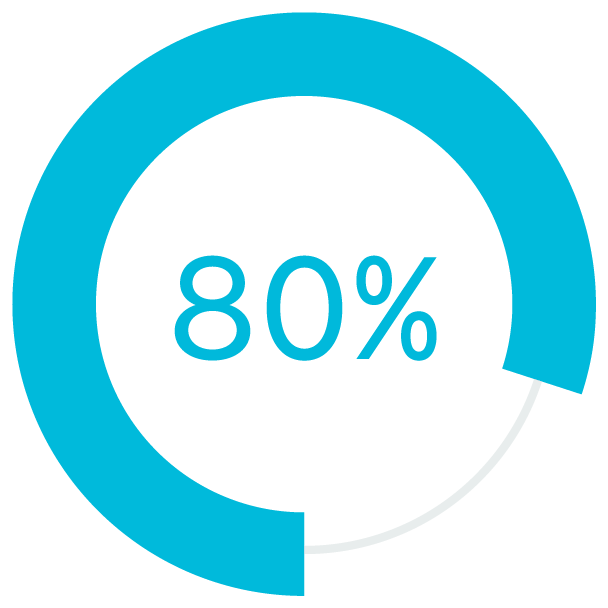
of workers prefer a hybrid work environment
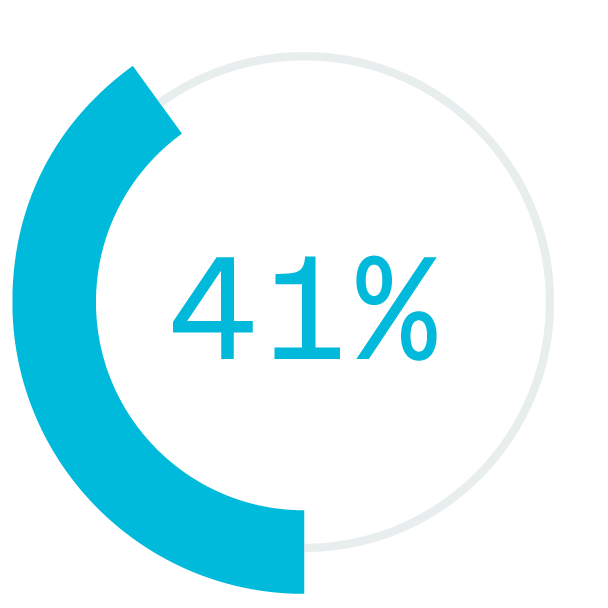
lower absenteeism
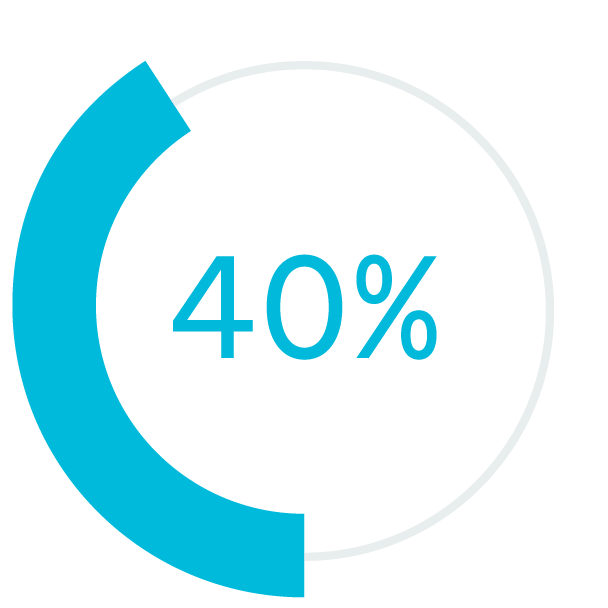
fewer quality defect
higher profitability
Something Powerful
Tell The Reader More
The headline and subheader tells us what you're offering, and the form header closes the deal. Over here you can explain why your offer is so great it's worth filling out a form for.
Remember:
- Bullets are great
- For spelling out benefits and
- Turning visitors into leads.
lower absenteeism
fewer quality defect
higher profitability
Text
Flexible work environments require access to on-premises systems and data, and therefore most enterprises rely on employees using a VPN. However, organizations can’t trust that workers will always use these secure channels. If an employee is using a mobile phone, he or she might forget to use the VPN and employ an unsecured wireless network instead, exposing corporate systems and data to risk.
During the pandemic, threat actors realized that insecure home networks and a lack of security controls typically found on corporate networks could work to their benefit. The World Economic Forum estimates cyber attacks jumped 238% globally between February and April 2020.
Technical Requirements
Secure Infrastructures
Flexible work environments require access to on-premises systems and data, and therefore most enterprises rely on employees using a VPN. However, organizations can’t trust that workers will always use these secure channels. If an employee is using a mobile phone, he or she might forget to use the VPN and employ an unsecured wireless network instead, exposing corporate systems and data to risk.
During the pandemic, threat actors realized that insecure home networks and a lack of security controls typically found on corporate networks could work to their benefit. The World Economic Forum estimates cyber attacks jumped 238% globally between February and April 2020.
Technical Requirements
Secure Infrastructures
Flexible work environments require access to on-premises systems and data, and therefore most enterprises rely on employees using a VPN. However, organizations can’t trust that workers will always use these secure channels. If an employee is using a mobile phone, he or she might forget to use the VPN and employ an unsecured wireless network instead, exposing corporate systems and data to risk.
During the pandemic, threat actors realized that insecure home networks and a lack of security controls typically found on corporate networks could work to their benefit. The World Economic Forum estimates cyber attacks jumped 238% globally between February and April 2020.
NEW ROLE OF THE CISO
Over 80% of security professionals believe social media, mobile messaging, or collaboration apps present medium to high risks to their organization.
SafeGuardCyber Survey April, 2019
Secure Infrastructures
Flexible work environments require access to on-premises systems and data, and therefore most enterprises rely on employees using a VPN. However, organizations can’t trust that workers will always use these secure channels. If an employee is using a mobile phone, he or she might forget to use the VPN and employ an unsecured wireless network instead, exposing corporate systems and data to risk.
During the pandemic, threat actors realized that insecure home networks and a lack of security controls typically found on corporate networks could work to their benefit. The World Economic Forum estimates cyber attacks jumped 238% globally between February and April 2020.
Text
Flexible work environments require access to on-premises systems and data, and therefore most enterprises rely on employees using a VPN. However, organizations can’t trust that workers will always use these secure channels. If an employee is using a mobile phone, he or she might forget to use the VPN and employ an unsecured wireless network instead, exposing corporate systems and data to risk.
During the pandemic, threat actors realized that insecure home networks and a lack of security controls typically found on corporate networks could work to their benefit. The World Economic Forum estimates cyber attacks jumped 238% globally between February and April 2020.
Organizations also increasingly rely on cloud-based collaboration platforms and personal communications technologies to connect teams across regions and time zones.
With the sudden onset of the pandemic, many organizations abruptly switched to remote work and found themselves having to allow technologies like MS Teams, Slack, Zoom and Webex on a scale they were uncomfortable permitting earlier. At the time, many IT leaders believed these solutions would be temporary and they’d quickly go back to "normal."
Now, more than a year later, not only are organizations continuing to use these technologies, but they’re doubling down. Yet, they still have no way to keep these systems secure from third-party risks. For example, a recent attack against EA Games involved infiltrating the company’s Slack instance and launching a fileless social engineering scheme to gain access to the network, resulting in the theft and exfiltration of highly-valuable intellectual property.
Similarly, IT once viewed communications solutions like WhatsApp and WeChat as personal apps. Because corporate teams had zero visibility into them, they would not allow employees to do business on them. But in some critical emerging markets, only a small percentage of people use email. Most use mobile chat applications like WhatsApp. It has become a business imperative to use the local technology.
New Security Challenges
These collaboration and communications tools present significant data governance and security challenges for large organizations. In a survey by SafeGuard Cyber:
- 78% of cybersecurity leaders express an inability to protect all communication channels and digital assets6
- 46% say collaboration tools represent the biggest security challenge
- 1 in 3 say their biggest challenge is mobile chat apps, WhatsApp, WeChat, Telegram
- 1 in 5 say their biggest challenge is Video meetings (Zoom, Webex, etc. )
Hybrid work environments will only increase the challenges. As employee devices and laptops move onto the corporate network and then back home where they can be exposed to hackers and more easily infected with malware and ransomware, it will be difficult for security teams to protect employees from threats, detect and respond to insider threats, or stop malware and ransomware.

Only 20% of security professionals feel confident they are effectively mitigating the digital risks from social media, messaging and collaboration apps.
SafeGuardCyber Survey April, 2019
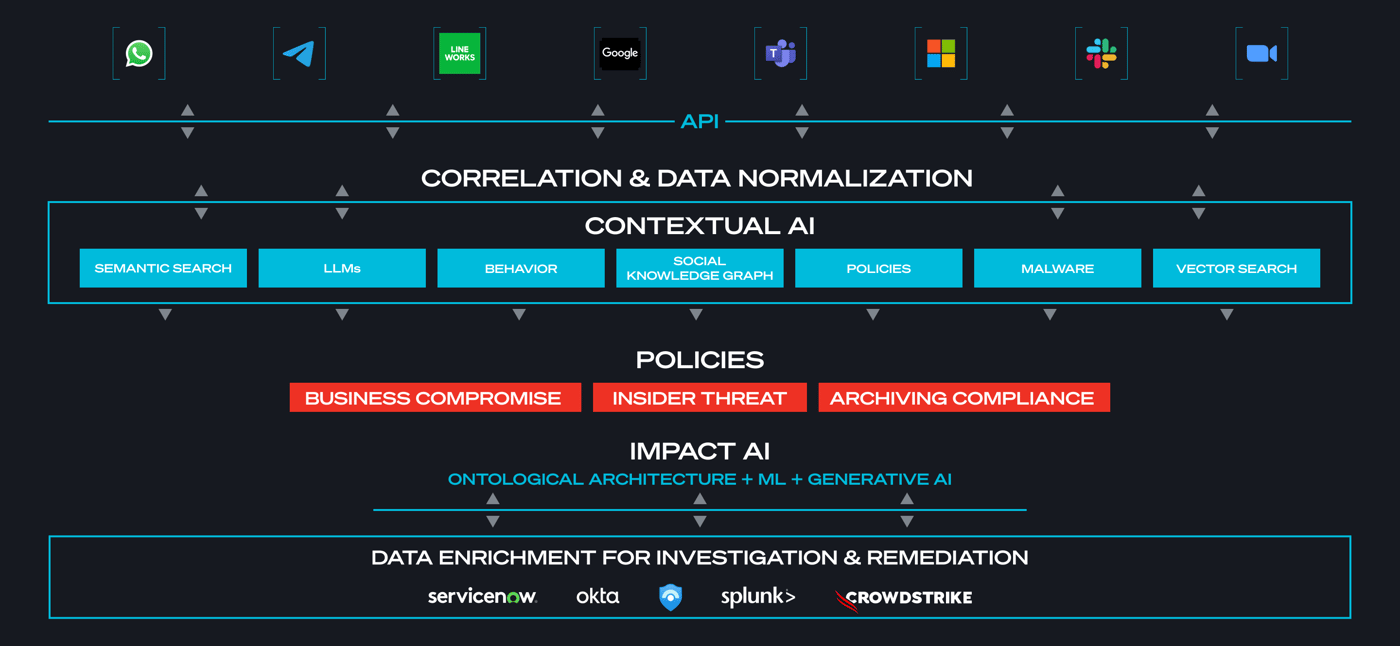
The Five Elements of Contextual AI
To close this blind spot in threat detection and stop attacks before they can do damage, SafeGuard Cyber uses Contextual AI, which combines five key components of a conversation:
 Semantic Analysis
Semantic Analysis
Extracts insightful information such as emotions, and sentiments to understand, interpret, and derive meanings from sentences and paragraphs. It uses machine learning to analyze the grammatical format of sentences, including the arrangement of words, phrases, and clauses to determine relationships between independent terms in a specific context. By examining the relationship between words in a sentence, semantic analysis helps provide a clear understanding of the context.
 Metadata Analysis
Metadata Analysis
Identifies message characteristics such as the sender’s address, receiver’s address, subject, and date, as well as Return-Path, Reply-To Field, and Message-ID. It identifies which servers, ISPs, and platforms the message has passed through, and can also determine if a message arrived at its intended recipient without faults or changes, and it can tell if files have been altered since they were first created.
 Digital Identity
Digital Identity
Is an accurate profile of a person created from a history of how, when, and why they use cloud communication channels. The profile builds a history of a person’s past connections, and can determine what is ‘normal’, such as talking to someone in HR every other week. If that person suddenly starts to communicate with someone in a different department, that may be considered anomalous behavior and worthy of further investigation.
 Behavioral Analysis
Behavioral Analysis
Examines all possible trends, patterns and activities of users to understand the difference between the expected and the unexpected. By understanding that a particular employee doesn’t send email at a certain time of day; doesn’t use email signatures; doesn’t misspell words; or doesn't send email from an unusual geographic location, unusual changes to these typical behaviors are quickly identified, and that person’s messages can be flagged for further analysis.
 Social Graph Analysis
Social Graph Analysis
Is a mapping of how people are communicating with each other. It builds a relationship model of people based on their patterns of communications. Unusual connections can be easily identified and combined with behavioral analysis to help detect account takeover and insider risk. Using Contextual AI, SafeGuard Cyber understands the who, why, and how of business communication, giving security teams the power to understand which communications may include social engineering attempts and helping protect organizations from costly and damaging business compromise (BC).


SafeGuard Cyber Differentiation
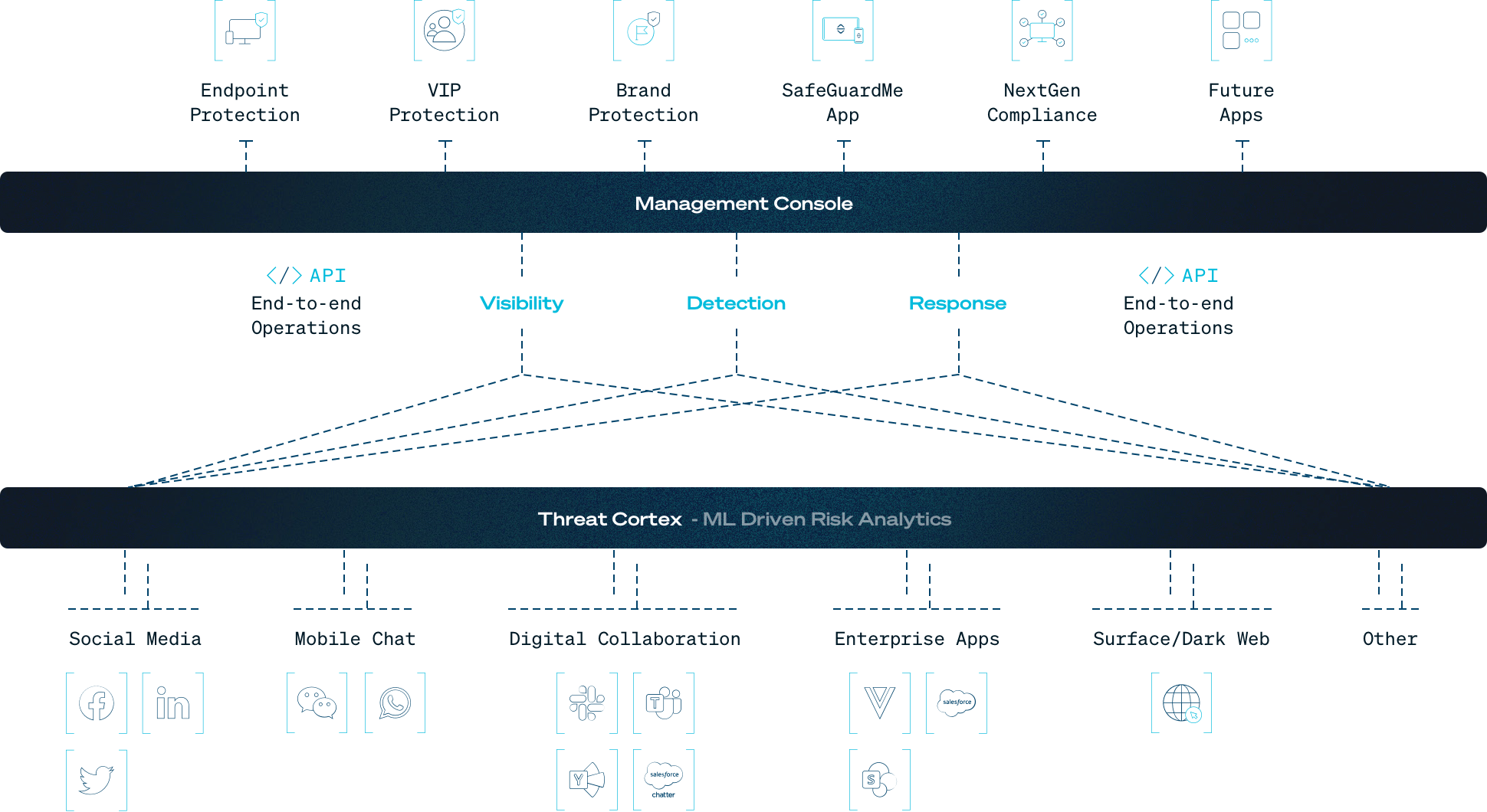
With its expertise in NLU and ML, SafeGuard Cyber provides unparalleled insights into the context and intent of communications. Our patented NLU technology and autodetection of 52 languages enable early threat detection, surpassing traditional behavioral approaches. Our platform’s cross-channel event correlation further enhances its capability to detect sophisticated threats across more than 30 digital channels.
Figure: By using machine learning to analyze the key elements of a conversation, SafeGuard Cyber helps security teams protect their business communications from social engineering, phishing, insider threats, and language-based attacks that evade legacy tooling.
SOC teams need the ability to identify and discover sophisticated social engineering attacks in all commonly-used cloud channels. SafeGuard Cyber helps by protecting more channels than any other security solution, providing Contextual AI for more than 30 digital channels including email, collaboration, chat, conferencing, social media, and mobile messages. Cross-channel event correlation builds upon this capability by comparing the content and context of messages across multiple cloud communication channels, enabling the platform to detect threats that siloed and less capable security tools miss.

SafeGuardCyber Survey April, 2019
SafeGuardCyber Survey April, 2019
SafeGuardCyber Survey April, 2019
Lorem ipsum dolor
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Nulla urna massa, maximus at neque vel, mollis efficitur.
Benefits
With SafeGuard Cyber’s agentless architecture, organizations benefit from:
Gain unprecedented visibility to respond to internal and external threats in hard-to-see places like direct messages and group channels. Reduce detection and response times in the cloud infrastructure where work gets done.
Be up and running in hours not days. Organizations no longer have to configure agents.
Connect our agentless security platform into your existing cyber defense systems, feeding event data and telemetry into your EDR and SIEM solutions.
Secure Human Connections
Ready to see how SafeGuard Cyber secures modern communication apps wherever they exist?
Expert Insights on Cloud App Risks
Stay up-to-date on the latest insider threats, ransomware, and third-party vulnerabilities.