
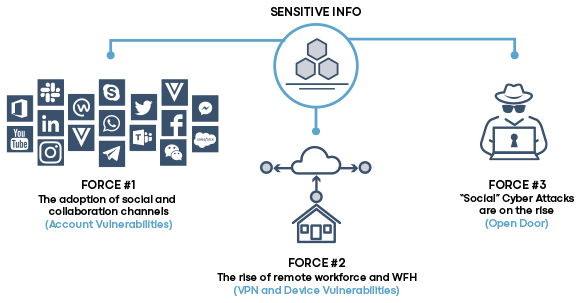
Email spear-phishing has long been a favorite vector of bad actors and has therefore been well-fortified against attack. While email security is a $3B industry, bad actors have shifted resources to carry out attacks against collaboration, chat, and social channels.
How are you safeguarding your modern digital communication channels?
Discover and onboard all authorized accounts for protection, inspect messaging for malicious
content, track new connection requests, and archive all account activity.
Monitor channels for suspicious activity and messaging; evaluate all file attachments and links for malware, and evaluate connections for known or suspicious bad actors.
Quarantine malware in real time, while sending IOC notification details to SOC/SIEM for evaluation to correlate social attacks with EDR. Leverage archive for actionable insights for the future.
Social media is now a favorite delivery vector for social engineering scams. How hackers profile their target victims.
Irwin Lazar, at Nemertes, shares how businesses are adjusting with WFH environments, and what a post-COVID workplace looks like.