Holiday Scammers to Capitalize on FOMO and Workplace Complexity
Cyber Monday now outpaces Black Friday in terms of sales, and cybercriminals are fine-tuning their phishing lures to take advantage of distracted users, including enterprise workforce employees.
Media broadcasting stories about economic headwinds and layoffs combined with complex workplace communications environments are combining to create the perfect conditions for phishing and social engineering attacks. Economic anxiety will likely be a contributing factor to people wanting to act quickly for the best deal. On top of that, workplace communication environments have rapidly grown more complex, with users toggling between multiple business communication tools, like email, Slack, Teams, SMS, and doing so across multiple devices.
Threat actors are honing their attack techniques to seize on the desire for deals coupled among a distracted workforce.
The Current Workplace Reality is Complex
Today’s work environment is varied across location, device, and myriad communication apps. A recent study looking at three Fortune 500 companies, found “the average user in the dataset toggled between different apps and websites nearly 1,200 times each day.”
This behavior adversely affects productivity, but also erodes the vigilance companies try to instill with security awareness training. The study notes, “excessive toggling increases the brain’s production of cortisol (the primary stress hormone), slows us down, and makes it harder to focus.”
The Work from Anywhere environment has also led to technical vulnerabilities in enterprise security as employees blur the lines between business and personal cloud communication applications.
In the SafeGuard Cyber platform, we’ve seen examples of retail-based phishing emails which can target employees through personal and professional accounts. Most of these links have so far led to account credential or credit card skimming sites. However, more ambitious threat actors can weaponize Cyber Monday to deploy more malicious attacks to gain a foothold in networks.
So what are common attributes that can help spot a cybercriminal spoofing a retailer? Based on data from SafeGuard Cyber, a provider of security and compliance solutions, the following retailers are most commonly spoofed.
Examples:
Target
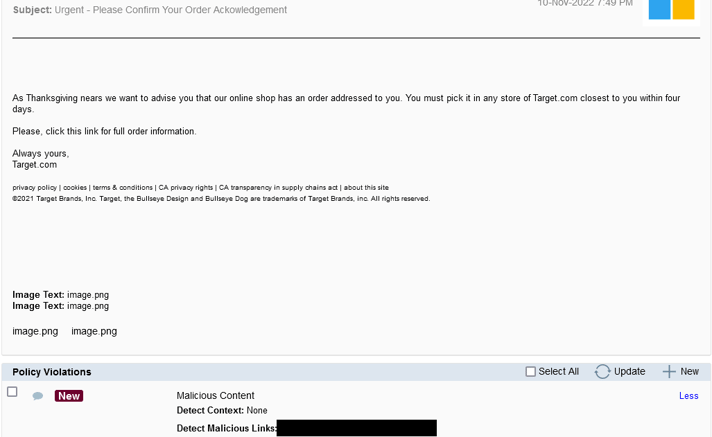
- Poses as coming from a popular retailer, where there is greater likelihood that the victim ordered from in the past
- Asking users to acknowledge an order preys on anxiety that inaction will lead to shipping delays
- Deadline of four days imposes urgency, a potent tactic with distracted users
Walmart
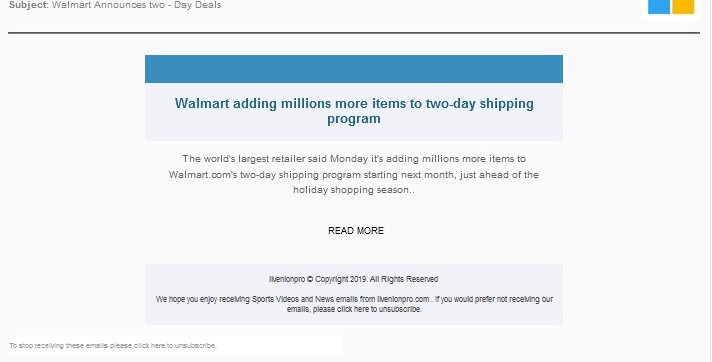
- The “announcement” looks to stand out from standard phishing emails.
- Reverse psychology makes the “Read More” call to action feel more innocuous
Walgreens
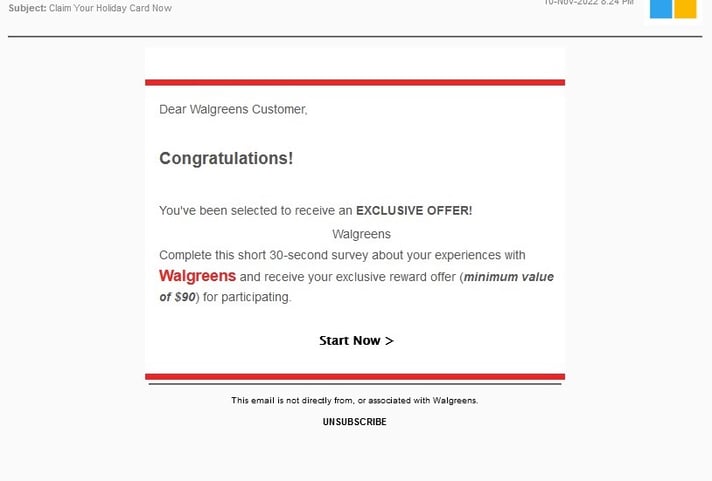
- Exclusivity plays to the psychology of gaining an advantage
- The link redirects attention to completing a survey rather than confirming an order
Other popular brands for impersonation include:
Tmobile, Best Buy, Amazon, Netflix, and Apple
Other Tactics Used by Cyber Criminals
And these are some others tactics being used:
- QR codes linking to malicious websites that are delivered via email addresses spoofed to look like they are coming from co-workers and friends to weaponize users’ trust.
- Offers for malicious Chrome extensions posing as automated coupon code collectors
- Phishing emails that claim problems with orders that target users in the week after Cyber Monday
Organizations must ensure they have robust cyber-resilience strategies in place, with adequate security controls to detect and prevent cyber threats across multiple channels of cloud communications.
These controls should include practical tools to detect social engineering tactics like urgency, language-based attacks in phishing scams, or account takeovers. Holiday shopping may not seem like the purview of corporate security. However, with workforces communicating in complex environments, distraction and distress can create a fertile ground for phishing campaigns. With the expansion of the working environment comes the expansion of the attack surface. Teams must be ready with technical controls, and they should work in tandem with awareness training staff to help employees understand the need to slow down and report anything suspicious.
If you are interested in learning more about the SafeGuard Cyber solution, you can take a quick 5-minute tour.
