Business Communications Compromise (BCC)
Begin your transformation to secure and compliant communication. Share your information so we can connect.

Download PDF
Executive Summary
Nearly half of all business communications today take place outside of traditional email. Attackers know this too, and are tailoring their attack mechanisms for well-known cloud workplace channels like Slack, Salesforce, LinkedIn, Zoom, WhatsApp, Telegram, and many more.
Attackers start messages in traditional email and then quickly move communications to cloud channels such as Slack or Teams. Using their social engineering skills, they can impersonate an executive and gain access to the corporate network to conduct invoice fraud or deliver a ransomware attack. By adding social engineering and language-based attacks to existing phishing schemes, bad actors are fundamentally changing the threat landscape.
To prevent business communications compromise (BCC) SOC teams need to be able to identify and discover sophisticated social engineering attacks in all your cloud channels. Visibility across multiple business communications channels and the tools to understand the context and intent of messages -- in both directions – can help prevent BCC from impacting your organization.
With deep visibility into 30 channels of business communications and the ability to understand more than 52 languages, SafeGuard Cyber correlates events across channels, allowing security organizations to have full visibility across all of their cloud workspace channels so they can respond faster and more effectively to stop ransomware, phishing, and other risks earlier in the kill chain.
Using patented Natural Language Understanding (NLU) technology, it quickly and accurately understands the context and intent of messaging across multiple cloud communication channels. By evaluating attributes such as lexical features, spelling features, and topical features, NLU identifies messages that are part of a social engineering attack. This lets you stop BCC attacks earlier in the kill chain.
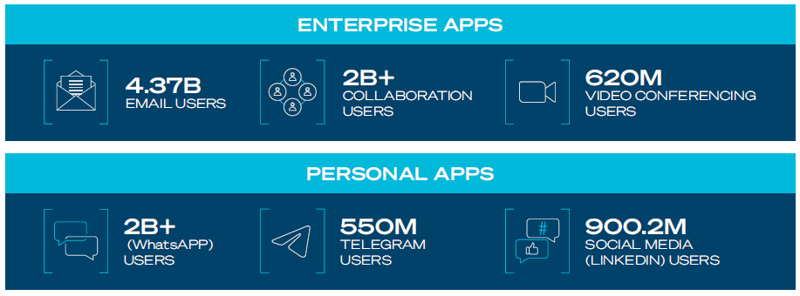
Although email remains a staple for business communications, the use of personal social media and mobile
messaging apps has jumped dramatically, driving a fundamental change to the threat landscape.
Communication channels such as Microsoft Teams, LinkedIn, and WhatsApp have superseded email as the preferred method of personal and professional communications in many organizations. By 2024, traditional in-person meetings are set to account for just 25% of team conversations; clearly illustrating how quickly businesses must shift from relying on physical interaction and embrace workflows facilitated through cutting-edge technology solutions. Since bad actors know that this is where their targets live and work, they are directing their attention here.
However, these communication channels remain vulnerable to spear phishing. While email security is a $3 billion industry, security solutions for workplace channels lag far behind. Most security teams don’t have tools developed specifically to protect the cloud workplace which typically lives outside the traditional security perimeter. These communication channels are vulnerable – and bad actors know it.
Even before the COVID-19 pandemic took hold, the shift toward WFH (work-from-home) protocols was well underway. A turbulent 2020 accelerated this trend; according to a Gartner survey, 74% of CFOs planned to shift employees to remote work permanently. But home offices are inherently less secure than traditional offices. (For example, in Q1 of 2020, spear phishers launched over 100,000 attacks against remote workers.) Home offices regularly deal with VPN issues, and often use legacy routers, PCs, and IoT devices. Safeguarding the future of work in a highly distributed remote environment is a complex challenge, which makes it easy for vulnerabilities to creep in.
The ongoing digital transformation is changing the way millions of people work and the tools they use to conduct business. In addition to email applications, remote workers are increasing their use of mobile-based instant messaging apps such WhatsApp, Facebook Messenger, and Telegram, and collaboration apps such as Zoom, Microsoft Teams, and Slack to their day-to-day routines.
Cloud communication tools help your employees connect with customers, colleagues, suppliers and financial institutions. But their popularity has opened up a new world of opportunities for cybercriminals. With the attack surface growing, business email compromise (BEC) is one element of a larger threat -- business communications compromise, or BCC.
Email phishing, the original form of cyberattack, first appeared in the 1990s. These attacks were carried out by scammers who posed as AOL employees, sending emails to AOL subscribers and asking them to “verify” their account or “confirm” their billing information. This approach to BEC is still in widespread use today.
Although businesses have become more aware of email-based phishing attacks and adopted solutions to identify these types of attacks, cyber criminals are constantly developing new, more sophisticated methods that take advantage of the proliferation of cloud communication apps to conduct their attacks. Attackers, especially those attempting to commit fraud, impersonation, and BCC, are evading detection by starting communications in email and then quickly moving conversations to other channels such as Slack or Teams.
By manipulating people into breaking security protocols, bad actors can gain access to an organization’s proprietary information, intellectual property, and financial resources.

Infiltrating your network is the goal of most attackers, and gaining access gives them a range of opportunities to cause damage your business. Cloud communications and collaboration tools are engaging and highly interactive, but they are typically used on unregulated personal devices such as mobile phones and tablets and aren’t protected with the same degree of security as corporate-owned devices. This makes personal devices more vulnerable to attackers and makes BCC attacks difficult to prevent.
For example, if attackers successfully gain access to an executive’s system through phishing or impersonation, they can direct staff to process unauthorized payments to their own accounts. Insiders with knowledge of your business and networks can also cause tremendous damage. In fact, the majority of breaches each year are the work of insiders, and the financial losses they cause continue to increase.
Sophisticated criminals are even creating fake video and audio messages in which they impersonate an organization’s executives. In these messages, which are sent via common communications channels, attackers can direct the accounts payable staff to make unauthorized payments directly to their account or create fraudulent invoices.
Stopping scams delivered through unregulated cloud channels is extremely challenging, and identifying and preventing attacks before they can inflict damage is critical for businesses to operate successfully.
w
w
Integrated cloud email security (ICES) solutions are commonly available, but today’s cloud workplace offers bad actors a multichannel attack surface. As Deloitte advised, “collaboration technologies… can pose serious threats to organizational security and privacy if not properly managed. As these technologies expand their reach and prevalence in business operations, organizations should keep a pulse on potential threats, enact controls where feasible, and promote service availability.”
Osterman Research, in a DarkReading article, advised that enterprises “should be looking for more capable solutions that detect and stop more phishing attacks, offer detection of advanced polymorphic and nested threats, and protect communication and collaboration tools via a holistic solution rather than being limited to protecting email only.”
Communication channels such as Microsoft Teams, LinkedIn, and WhatsApp are rapidly superseding email as the preferred method of personal and professional communications in many organizations. Over half of US workers rely on workplace collaboration tools to carry out their job duties - and that’s being reflected by employers too, with 56% using online tools and social media platforms to keep up communication. Since bad actors know that this is where their targets live and work, they are directing their attention here.
However, these communication channels remain vulnerable to spear phishing. While email security is a $3 billion industry, security solutions for cloud workplace channels lag far behind. Most security teams don’t have tools developed specifically to protect the cloud workplace which typically lives outside the traditional security perimeter. These communication channels are vulnerable – and bad actors know it.
The rapid expansion of cloud collaboration, chat, conferencing, and social media apps, in addition to email, has coincided with a huge increase in the number of data breaches. While some of these breaches are driven by internal employees, 80% of breaches being caused by those external to the organization. (2022 Verizon DBIR)
The SafeGuard Cyber platform is driven by a patented NLU detection engine that, along with deep visibility into multiple channels, provides contextual analysis of attempted attacks and delivers rapid response capabilities across communication channels. SafeGuard Cyber security protects more than 30 communication channels from language-based and social engineering attacks.
According to research from the Business Information Industry Association (BIIA), language-based attacks are now the new normal for business email compromises (BECs); nearly 75% of attacks use language as the main attack vector. In addition to language, malicious links, weaponized payloads, and common business workflows have become target for attackers to compromise employees and steal money, credentials, or sensitive data.
Determining user identity, behavior analytics, context, and intent must be integral to your protective mechanisms. Suspicious attachments, poor grammar and format, and generic signatures and greetings can be indications of ongoing social engineering exploits. With its patented Natural Language Understanding (NLU) technology, SafeGuard Cyber can quickly determine the context and intent of communications in cloud communication channels – both inbound and outbound. By evaluating attributes such as lexical features, spelling features, and topical features, NLU can determine the likelihood that the source message is a social engineering attack.
SafeGuard Cyber is expert in developing accurate, scalable contextual analytics for security and compliance, offering:
- Visibility into inbound and outbound communications in Microsoft 365 email and 30 other business channels for collaboration, chat, conferencing, social media, and mobile messaging.
- Cross-Channel Event Correlation helps detect attack campaigns that involve lateral movement across communication channels.
- Azure AD and Okta integration provide reauthentication response action detections that other solutions miss.
- Patented, third-generation NLU technology, with autodetection of 52 languages and cloud-based machine learning, provides insight into the context and intent of communications to detect threats earlier than pure behavioral approaches.
- Out-of-the-box detections for social engineering attacks, malicious links, malware attachments, & improper business conduct.
- Automated response via IAM re-authentication and message quarantine
Safeguard Cyber security can detect and stop business communications compromise attacks that target human psychology and behavior to slip past existing threat detection solutions or evade early kill chain detection. It fills the security gap that exists beyond email to protect business channels for collaboration, chat, conferencing, social media, and mobile chat, and offers security teams more time and capabilities to protect the cloud workspace.
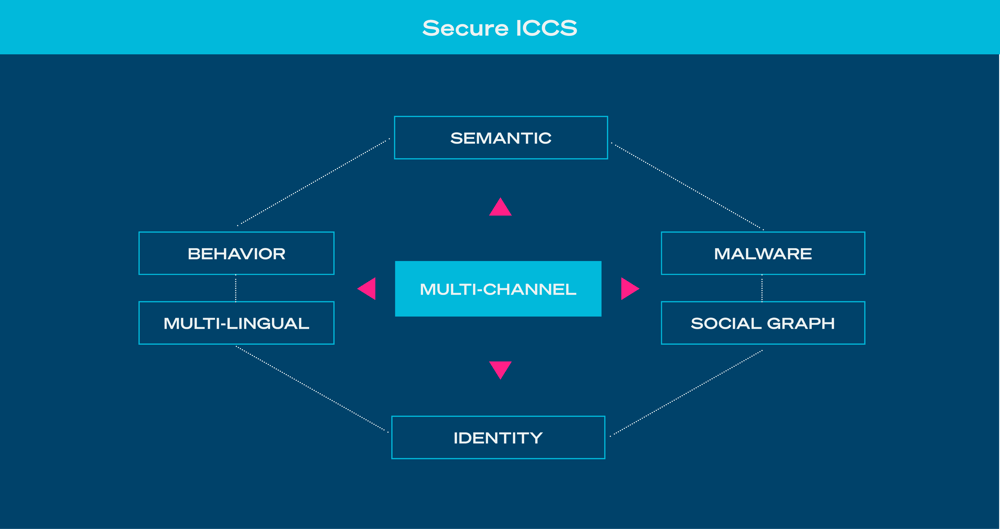
By understanding how humans interact, SafeGuard Cyber can detect attempts at business communication compromise. The Threat Cortex Detection Engine is core to the platform, using patented capabilities to detect social engineering attacks by analyzing a comprehensive set of message features, including:
- Digital Identity – verifying the sender’s identity
- Semantic Analysis – understanding the content of the message
- Metadata Traits – analyzing characteristics of the message
- Behavior Analytics – identifying abnormal behavior
- Social Graph Analysis– analyzing the history of past communications
When it comes to ransomware, avoiding becoming a victim is better than cure. Reducing the risk of ransomware incidents should be a priority for many businesses. However, should an organization be unfortunate enough and fall prey to ransomware, the following steps should be followed:
-
Remove The Device From The Network.
Ransomware on one device is bad, but ransomware proliferating through a network of devices is catastrophic. Employees should be trained to immediately disconnect their device from the network if they see a ransomware demand displayed on their screen. They should also do the same if they observe anything peculiar, such as an inability to access their own files. Employees must not attempt to restart the device; it should be sent immediately to the IT department. -
Notify Law Enforcement.
Ransomware is a crime. Theft and extortion rolled into one make it a law enforcement concern. Organizations should all default to immediately contacting the police cybercrime department, should they fall victim to a ransomware attack. -
Use Digital Risk Protection to Establish The Scope of Attack.
In the wake of a ransomware attack, security teams need to gather as much intelligence as they can, as fast as they can. This will help both internal IT teams and law enforcement agencies formulate a response. Enterprises should strive to figure out the nature of the attack: who is behind it, what tools they used, who they targeted and why. Answering such questions can help your IT managers and network administrators figure out the extent of the attack and protect networks from future attacks. -
Consult with Stakeholders to Develop the Proper Response.
Enterprises suffering a bad ransomware attack need to answer a host of questions: Can they afford to lose access to the targeted files, either because they have been backed up, or because they are not of the highest priority? Can the organization afford the ransom? Is there any room for negotiation? All stakeholders, from shareholders to legal counsel, should be consulted. -
Get the Post-Mortem Right.
The best way to resist a ransomware threat is to have learnt from the last one. After an attack, enterprises should task their IT technicians, network administrators, and cybersecurity teams with a thorough review of the breach. A meticulous assessment of an organization's infrastructure, practices, and processes is required to discover flaws in security, and reinforce an enterprise against existing and future threats.
Fortunately, more companies are becoming smart enough to not give in to the threat of ransomware. As of Q4 of 2020, the average ransom payment is down by 34% ($154,108) from $233,817 in 2020’s Q3.
The dramatic decline can be attributed to the recent instances of malware attacks where, instead of being deleted, the stolen data is released publicly, even when the affected organization or individual pays. Now, more victims of cyber extortion are saying “no” to ransom payments, and are becoming smarter in their cybersecurity efforts by creating backups of their data and following best practices.
Hopefully, moving forward, more companies will proactively secure their data by following the best practices stated above and continue to resist being strong-armed by ransomware attackers. When cyber extortion loses its profitability, organizations win.
With proper communication risk protection, organizations can detect and nullify ransomware threats before they become an issue. The SafeGuard Cyber platform can keep pace with the scale and velocity of modern digital communications, and detect phishing links and other indicators of ransomware attacks across the full suite of cloud applications. Threats are instantly flagged and quarantined before an unsuspecting human target clicks on anything dangerous.
Secure Human Connections
Ready to see how SafeGuard Cyber secures modern communication apps wherever they exist?
Expert Insights on Cloud App Risks
Stay up-to-date on the latest social engineering, insider threats, and ransomware vulnerabilities.



