The Lazarus Group (assigned the moniker “ZINC” by Microsoft) is an advanced persistent threat (APT) group that’s been wreaking havoc in the cybersecurity world since 2009.
This North Korea-based threat actor continues to make waves. Since June of this year, Lazarus has continued compromising individuals with LinkedIn phishing scams, employing traditional social engineering tactics, and moving the conversation to WhatsApp for the delivery of malicious payloads.
Let’s learn more about this multichannel phishing campaign, how it weaponizes open-source software, and what enterprises can do to protect themselves.
Lazarus Group’s Multichannel Phishing Modus Operandi
In June of 2022, LinkedIn Threat Prevention and Defense detected the group creating fake profiles to target technical support professionals and engineers employed at media and IT companies in the US, UK, and India.
These “profiles” claim to be recruiters working for technology, defense, and media entertainment companies. Lazarus tailored its LinkedIn phishing outreach to the profession or background of the targets, encouraging them to “apply for an open position at one of several legitimate companies.” Lazarus has successfully used this tactic for years.
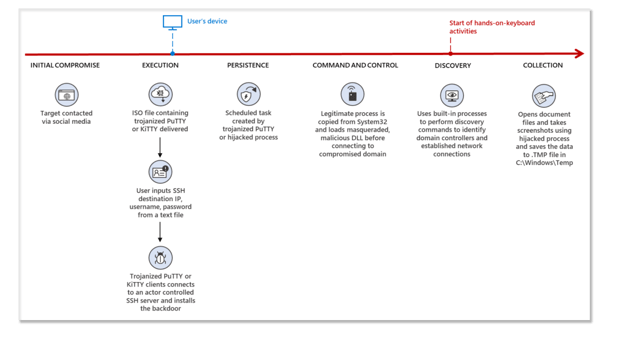
The attack flow diagram of a Lazarus LinkedIn scam (Courtesy of Microsoft)
Once they’ve established rapport and trust, the “recruiters” moved the conversation away from LinkedIn to the encrypted messaging app WhatsApp under the guise of sending them the “requirements” necessary for the “job application” on a more secure channel. Here, Lazarus drops its malware to infect victims and steal their data and credentials.
Disrupt Social Engineering Attacks Earlier in the Kill Chain
What makes these multichannel phishing campaigns so effective? It’s because social engineering attacks target humans, NOT systems.
Nowadays, it’s easier to find solutions that reinforce an enterprise’s security or cover some of the system gaps of the widespread adoption of cloud-based communications. Multi-Factor authentication, hardware security keys, and legacy security awareness training are still viable frontline defenses to establish a layer of cybersecurity.
However, the resurgence of social engineering exposes a critical vulnerability in any enterprise – humans. The human eye and mind did not evolve towards suspicion, so most multichannel phishing and social engineering attacks cloaked in simple, unassuming words escape scrutiny.
“We know that human beings are always the most vulnerable element of any cybersecurity strategy. No matter how much training we do, no matter how much awareness is created, human beings are somewhat naive, and the human eye can’t detect a lot of the more sophisticated attacks that they face on a day-to-day basis.”
- SafeGuard Cyber CEO Chris Lehman, in his Nasdaq Trade Talks interview about cybersecurity and Natural Language Understanding (NLU)
Social engineers create these language-based attacks and design them to impersonate someone you trust: a colleague, or a figure with a significant position in the company. This deception can lead to serious damage.
“82% of all breaches that happened last year [2021] were the result of the exploit of human vulnerability.”
Natural Language Understanding: A Game-Changer
Legacy network tools and solutions like firewalls and EDR can stop malware. However, businesses and enterprises must disrupt social engineering and phishing attacks early, especially during the initial compromise phase. Natural Language Understanding (NLU) is changing the game in favor of cybersecurity teams and professionals.
During his Nasdaq Trade Talks interview, Chris Lehman, CEO of SafeGuard Cyber explained how NLU benefits companies:
“What Natural Language Understanding does is actually look inside of these communication channels and analyze the text of the conversation itself. So we can detect threats that are language-based that traditional security technologies just weren’t designed to pick up or detect.”
Traditional cybersecurity tools rely on metadata-based behavioral analysis, looking at account behavior and anomalous activity. NLU analyzes the language-based elements in a Slack or Teams conversation, including lexical features, context, and topical elements. They are automatically analyzed and evaluated against models for the identification and prevention of social engineering attacks. For example, an email or Slack message will be flagged if it pushes urgency or demonstrates persuasion techniques within the language itself.
NLU helps security teams apply technical controls that combat multichannel phishing and social engineering, where none existed before. With this visibility across channels and NLU analysis of context and intent, organizations can respond faster and stop attacks earlier in the kill chain. This is a defense-in-depth approach to thwart the newest iteration of social engineering TTPs that have led to so many devastating breaches over the last two years.
The SafeGuard Cyber platform leverages a combination of ML and NLU to ensure the security of enterprise communication channels. This added layer of protection helps companies defend against threat actors like Lazarus.
If you are interested in learning more about the SafeGuard Cyber solution, you can take a quick 5-minute tour.

.jpg)