Executive Summary
- The Prynt Stealer malware, discovered for sale on underground forums by researchers at Cyble, has the ability to steal credentials and data from multiple browsers, messaging applications and other services (including Telegram).
- Because of its connection to messaging applications, actors who purchase this malware may attempt to propagate it through these channels or use accounts compromised through the malware to target contacts of the victim.
- SafeGuard Cyber tested sending the malware to a SafeGuard Cyber protected messaging account and detected and alerted on the malicious file.
Background
On April 21, 2022, researchers at Cyble posted the technical analysis of a new info-stealer malware called Prynt Stealer. The malware was available for purchase on underground forums on a license model, at a low cost of $100 for a one year license and $900 for lifetime use. The malware has the ability to steal web data, login data, session cookies, historical data, and other data for web browsers, VPNs, FTP services, gaming applications, and messaging applications. Cyble’s technical report breaks down how the malware works and how to defend against it from a technical level and we would highly recommend defenders review the report.
Guide: Learn how to mitigate
the risks of ransomware attacks
Event Analysis
The malware is of particular interest to SafeGuard Cyber as there are multiple ways in which it can be used to target the messaging applications that we help protect. First, in the case of Telegram, the malware directly steals data stored by the application on the victim's computer, which may include login data and other sensitive information. Second, the malware targets session cookies stored on various web browsers. These session cookies can be used to gain access to other messaging applications like Slack, which also have a web-based client. There is also a history of actors using session cookies to compromise messaging applications, like the 2021 EA breach.
Due to these messaging application capabilities, we believe that actors who buy this malware may target victims on these channels directly or utilize these channels after an initial compromise to continue to propagate their malware. Especially in the case of Telegram, the actor may attempt to target a user on the messaging platform directly to ensure that the victim's machine has access to the Telegram data that they can then steal. Then in the case of any other messaging application from which an actor may gain session cookies/credentials, they could use the compromised account to further propagate the malware in these highly trusted communication channels. This could allow them to possibly move laterally within an organization that the victim is a part of and turn the attack from an individual compromise to an enterprise targeting attack.
In these cases, the odds are in the malicious actor’s favor as communication on these channels (especially Slack) tends to be of higher trust than random emails, and there are little to no native detection and alerting capabilities for malicious files or social engineering language within the platforms themselves.
As SafeGuard Cyber's mission is to ensure security on these platforms we decided to test sending the malware to a SafeGuard Cyber-protected account. We acquired a sample of the malware, zipped it to provide further obfuscation, and sent it to an account with SafeGuard Cyber protection.
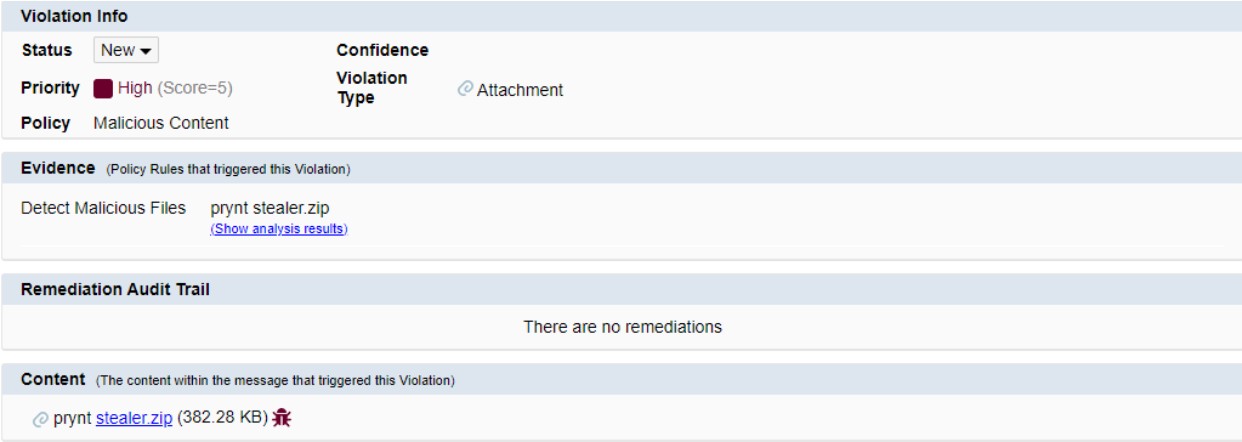
The platform successfully detected the malicious file and alerted it to the enterprise.
Then in regards to the social engineering that may accompany a message delivering this malware, while every actor who purchases this malware will likely have their own unique lures, SafeGuard Cyber also provides Natural Language Understanding (NLU) capabilities for messages received and sent on these applications. These NLP detections can be used to alert on possible campaigns like these while in the pretexting stage.
If you are interested in learning more about the SafeGuard Cyber solution, you can take a quick 5-minute tour.

