Beyond Email:
New Business Communication Risks
Begin your transformation to secure and compliant communication. Share your information so we can connect.

Download Sample Risk Report
Executive Summary
In every proof of value (POV) SafeGuard Cyber performs, we provide a summary of the risk events and detection types discovered during the POV period. The Risk Report is unique to every customer's business communications environment, and breaks down risk trends by each communication channel (e.g., M365 email, Slack, etc.). The report provides actionable recommendations that can be adopted to mitigate business communication risks.
In this example Risk Report, we have anonymized the data gathered over a two-week period from a real customer and outlined some of the findings. You can download the full sample report to see the more comprehensive analysis.
In this particular POV, the customer's environment faced continual exposure to a variety of risk factors, including one notable spear-phishing attack that evaded the existing SEG, and leakage of PII.
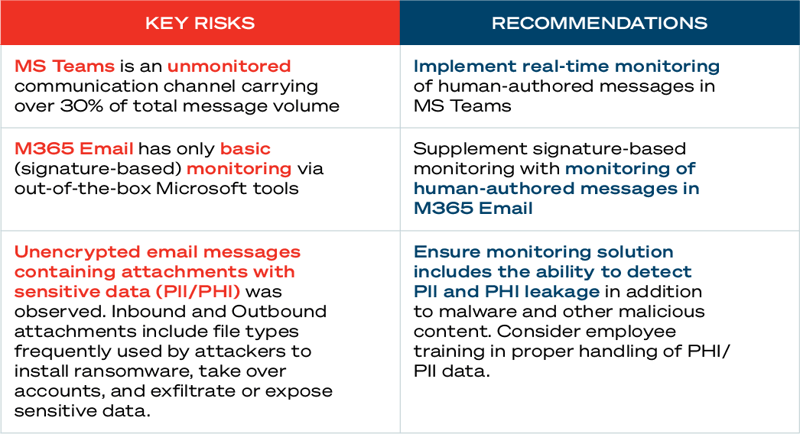
Here is a sample summary table of key risks and recommendations. The totality of detection is used to provide an overall risk level.
A Spear-phishing attempt was detected. While the initial presentation of the message appeared to be a relatively unsophisticated attempt at financial fraud via the efax.com distribution group, a deeper investigation revealed it to instead be an attempted malware/ransomware attack (More details on this attack can be found below).
A leakage of sensitive data was detected. In this example, the exposed PII included: the patient’s Utility Bill, Loan Statement, Driver’s License, and Enterprise Master Patient Index (EMPI) number, as well as an IRS W-9 form with the EIN of the lender.

of all business communications for this customer occurred in an Unmonitored Channel (MS Teams)
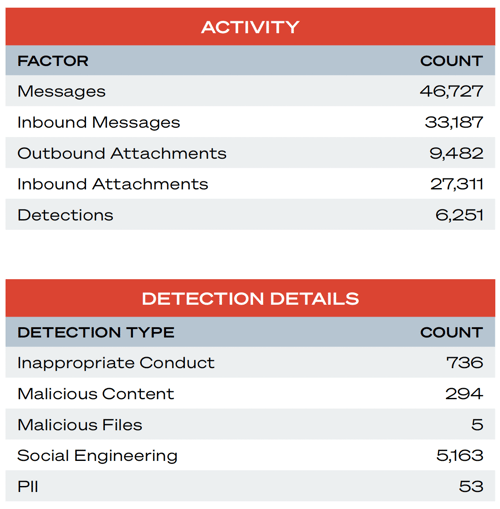
Inbound Attachments, further broken down by file type to quantify the continuous stream of risk to the customer
Outbound Attachments, to quantify the potential avenue of data exfiltration and/or IP loss
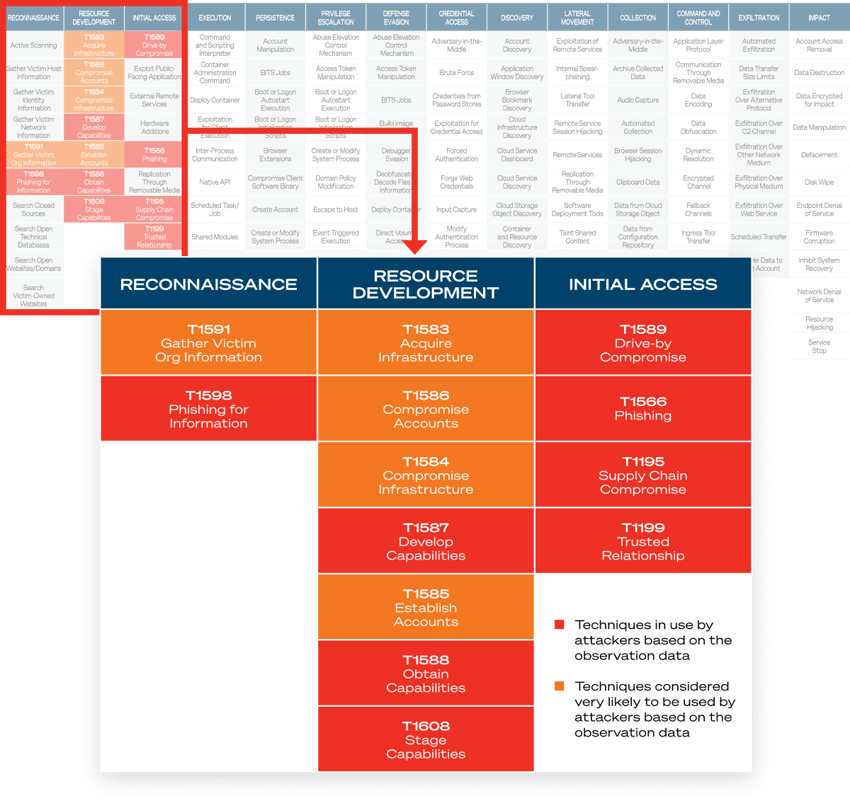
MITRE ATT&CK® Matrix
High-risk detections are mapped against the MITRE ATT&CK® framework for easier analysis of TTPs and potential compromise.

“I've not only gained insight into all the communications in my organization, but also oversight -- catching unencrypted emails, catching phishing emails that made it past the spam filter, knowing who our highest risk personnel are, catching social engineering attacks, and more.”
Director of IT & Security


M365 Email Channel Details
In this sample, we summarize the risks by critical communications channel. Here, we look at the customer's M365 instance for the POV time period. This section includes a detailed analysis of a spear-phishing attack that evaded the SEG.
Summary
While other communication platforms are rapidly being adopted by attackers, email still remains the single most commonly-used attack channel. The large number of inbound attachments (27,311) represents a constant threat of account compromise, malware and ransomware, and other threats. Email is also a well-used channel for Social Engineering, which poses threats such as account compromise, lateral movement, privilege escalation, and payment fraud.

M365 Email | Notable Detections
Social Engineering – Detect Social Engineering Attacks
 MITRE ATT&CK Technique:
MITRE ATT&CK Technique:
T1566 – Phishing / T1566.002 - Spear-phishing Link
Detection Overview
Sophisticated example of social engineering detected. The timeline of this event is as follows:
First user signed up for an eFax account:
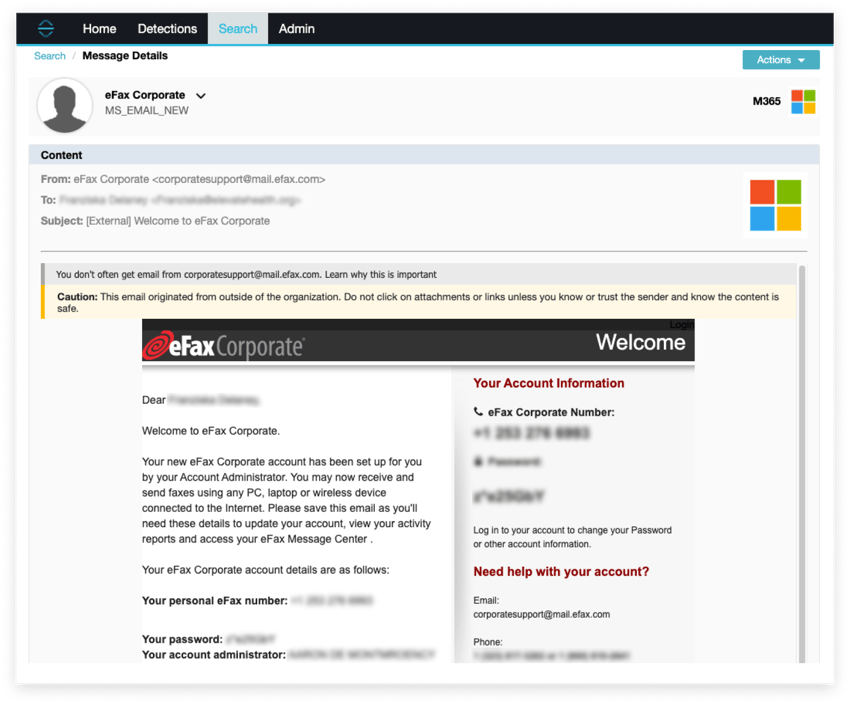
Almost immediately, an email came in to message@inbound.efax.com
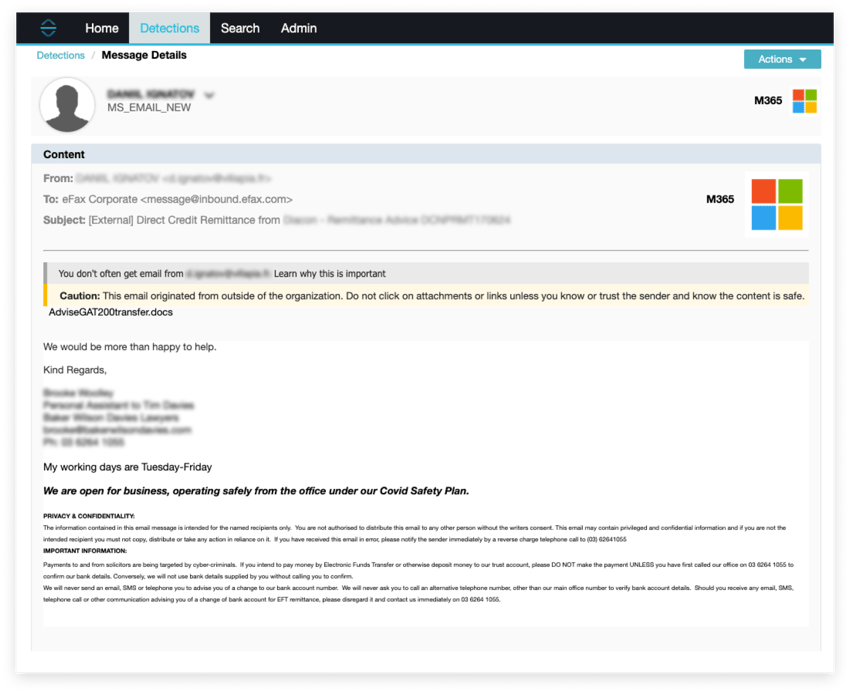
This email on its surface appears to be a fairly unsophisticated invoice fraud Spear-phishing attempt, with a link to a website, upon which a blurred image of a supposed invoice is displayed, with a call to action for the user to click “Open” to display it.
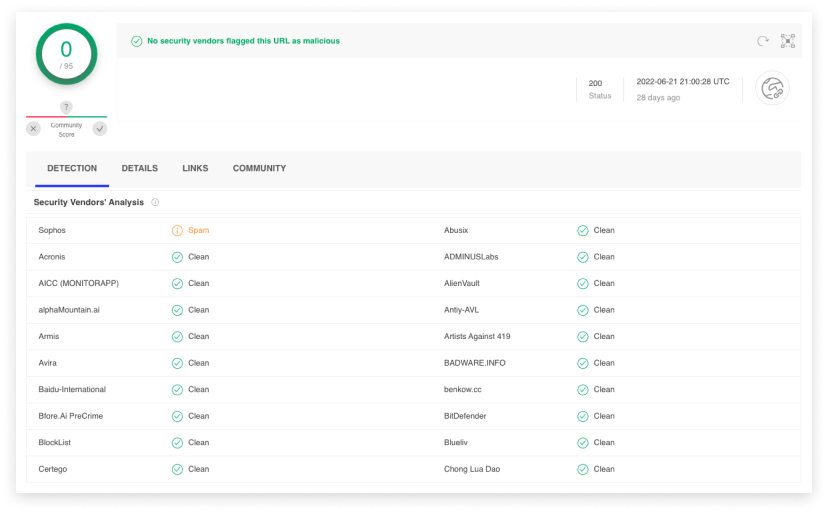
The initial domain comes up clean in a VirusTotal scan:
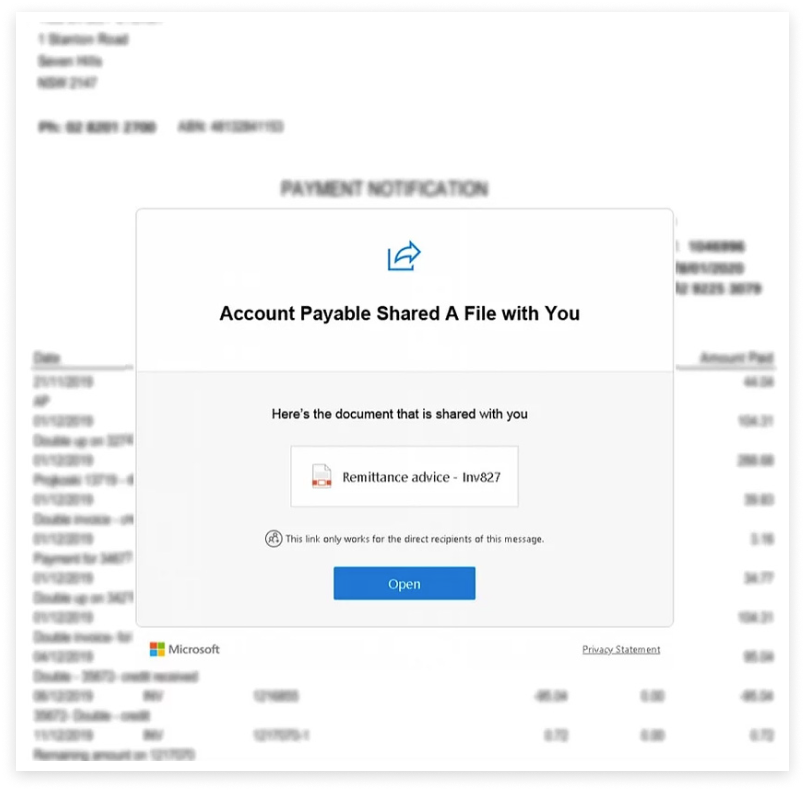
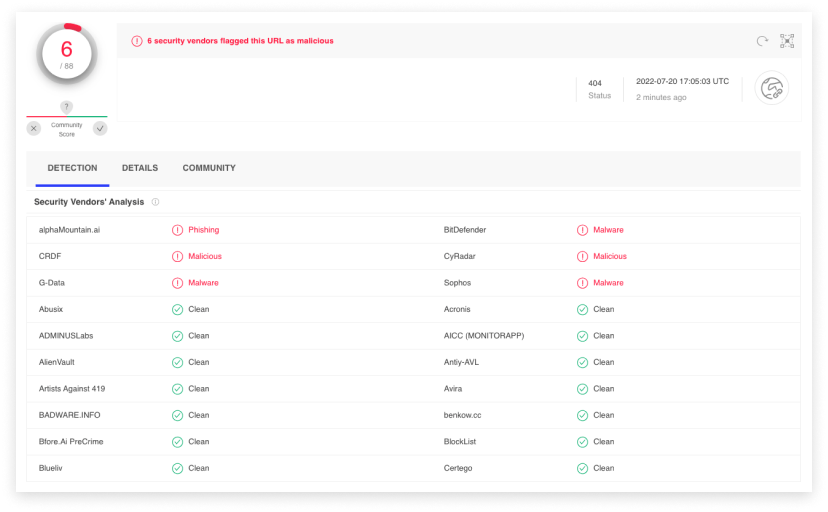
But if the user clicks the “Open” link on the page, they are taken to a website which flags as malicious in VirusTotal:

Microsoft Teams | Channel Details
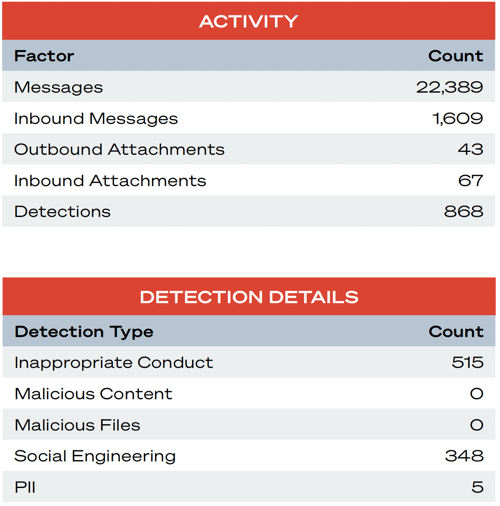
Here, we look at the Teams instance, where many customers indicate they have no visibility. This section includes a summary of detections to help customers quantify their risk exposure.
Summary
The presence of external messages in MS Teams increases risk to the organization. Potential negative outcomes include malware and ransomware, data theft/leakage, and social engineering. The lack of external attachments during the observation period reduced the risk level in this analysis, but the external attachments are still possible and may cause harm in the future. A relatively high number (515) of Inappropriate Conduct Detections expose the organization to potential legal action, negative reviews on company rating websites, low morale, and reduced productivity.


Secure Human Connections
Ready to see how SafeGuard Cyber secures modern communication apps wherever they exist?
Expert Insights on Cloud App Risks
Stay up-to-date on the latest insider threats, ransomware, and third-party vulnerabilities.

