Executive Summary
Humans are the most vulnerable part of any organization's cybersecurity defenses. The growing remote workforce and expanding use of digital communication channels is helping bad actors renew their efforts to steal data and extort funds with adapted tactics. With 45% of business communications occurring outside of email in channels such as Teams or Slack, to personal apps like LinkedIn, attackers are increasingly using social engineering and other language based attacks to skirt around existing email security solutions.
Attacks come in many shapes and forms, from ransomware and account takeover, to fraud, business email compromise (BEC), ransomware, and more. To counter these threats, organizations need to retool their security systems to gain full visibility across all workspace channels and enable the use of NLU-based (Natural Language Understanding) Context Analysis to understand the context and intent of business communications.
year on year deepfake attacks are on the rise
of CISO’s expected more serious attacks via the cloud in 2023, indicating a shift in threat landscapes.
The Changing Nature of Work
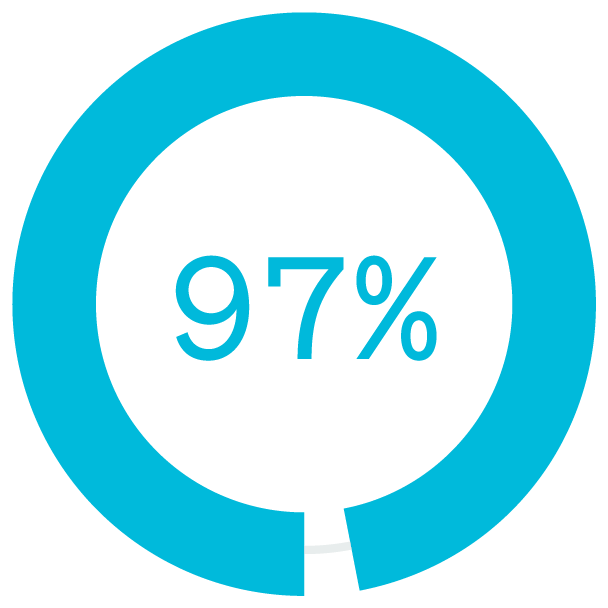
of North American office workers worked from home more than one day per week
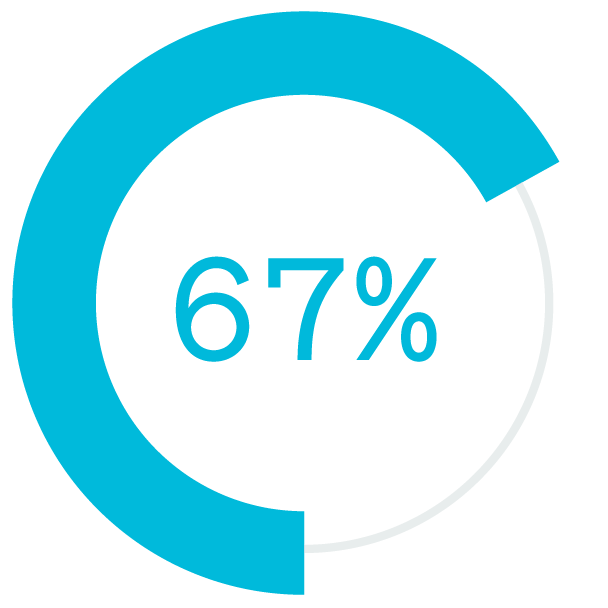
had not worked remotely prior to COVID-19
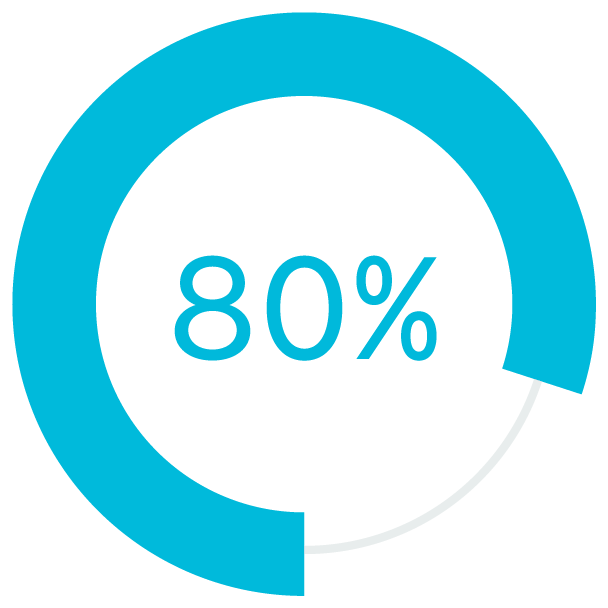
of workers prefer a hybrid work environment
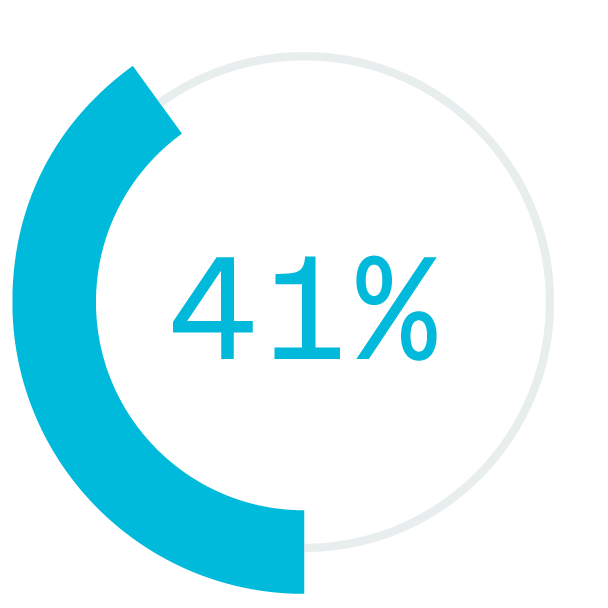
lower absenteeism
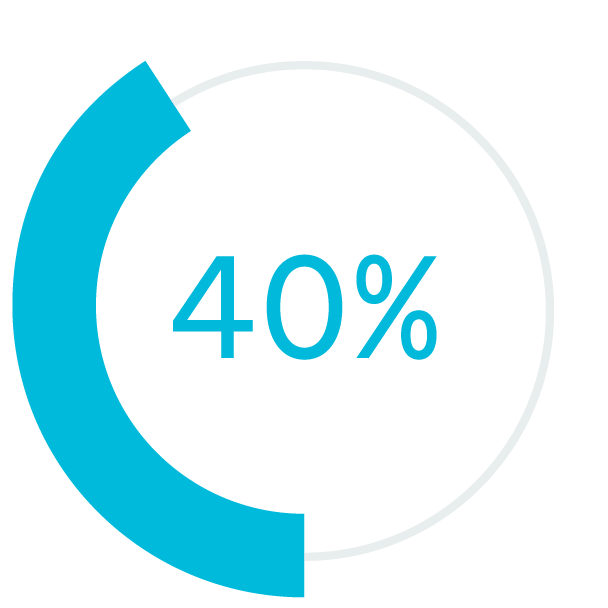
fewer quality defect
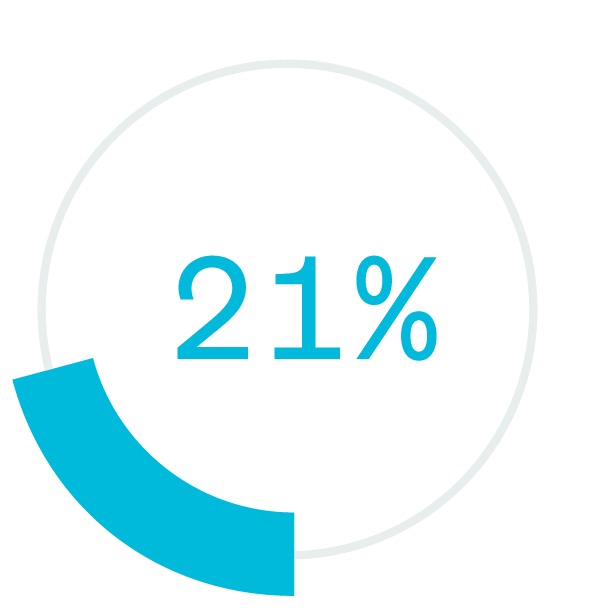
higher profitability
Something Powerful
Tell The Reader More
The headline and subheader tells us what you're offering, and the form header closes the deal. Over here you can explain why your offer is so great it's worth filling out a form for.
Remember:
- Bullets are great
- For spelling out benefits and
- Turning visitors into leads.
lower absenteeism
fewer quality defect
higher profitability
Text
Flexible work environments require access to on-premises systems and data, and therefore most enterprises rely on employees using a VPN. However, organizations can’t trust that workers will always use these secure channels. If an employee is using a mobile phone, he or she might forget to use the VPN and employ an unsecured wireless network instead, exposing corporate systems and data to risk.
During the pandemic, threat actors realized that insecure home networks and a lack of security controls typically found on corporate networks could work to their benefit. The World Economic Forum estimates cyber attacks jumped 238% globally between February and April 2020.
Technical Requirements
Secure Infrastructures
Flexible work environments require access to on-premises systems and data, and therefore most enterprises rely on employees using a VPN. However, organizations can’t trust that workers will always use these secure channels. If an employee is using a mobile phone, he or she might forget to use the VPN and employ an unsecured wireless network instead, exposing corporate systems and data to risk.
During the pandemic, threat actors realized that insecure home networks and a lack of security controls typically found on corporate networks could work to their benefit. The World Economic Forum estimates cyber attacks jumped 238% globally between February and April 2020.
Technical Requirements
Secure Infrastructures
Flexible work environments require access to on-premises systems and data, and therefore most enterprises rely on employees using a VPN. However, organizations can’t trust that workers will always use these secure channels. If an employee is using a mobile phone, he or she might forget to use the VPN and employ an unsecured wireless network instead, exposing corporate systems and data to risk.
During the pandemic, threat actors realized that insecure home networks and a lack of security controls typically found on corporate networks could work to their benefit. The World Economic Forum estimates cyber attacks jumped 238% globally between February and April 2020.
NEW ROLE OF THE CISO
Over 80% of security professionals believe social media, mobile messaging, or collaboration apps present medium to high risks to their organization.
SafeGuardCyber Survey April, 2019
Secure Infrastructures
Flexible work environments require access to on-premises systems and data, and therefore most enterprises rely on employees using a VPN. However, organizations can’t trust that workers will always use these secure channels. If an employee is using a mobile phone, he or she might forget to use the VPN and employ an unsecured wireless network instead, exposing corporate systems and data to risk.
During the pandemic, threat actors realized that insecure home networks and a lack of security controls typically found on corporate networks could work to their benefit. The World Economic Forum estimates cyber attacks jumped 238% globally between February and April 2020.
Text
Flexible work environments require access to on-premises systems and data, and therefore most enterprises rely on employees using a VPN. However, organizations can’t trust that workers will always use these secure channels. If an employee is using a mobile phone, he or she might forget to use the VPN and employ an unsecured wireless network instead, exposing corporate systems and data to risk.
During the pandemic, threat actors realized that insecure home networks and a lack of security controls typically found on corporate networks could work to their benefit. The World Economic Forum estimates cyber attacks jumped 238% globally between February and April 2020.
Organizations also increasingly rely on cloud-based collaboration platforms and personal communications technologies to connect teams across regions and time zones.
With the sudden onset of the pandemic, many organizations abruptly switched to remote work and found themselves having to allow technologies like MS Teams, Slack, Zoom and Webex on a scale they were uncomfortable permitting earlier. At the time, many IT leaders believed these solutions would be temporary and they’d quickly go back to "normal."
Now, more than a year later, not only are organizations continuing to use these technologies, but they’re doubling down. Yet, they still have no way to keep these systems secure from third-party risks. For example, a recent attack against EA Games involved infiltrating the company’s Slack instance and launching a fileless social engineering scheme to gain access to the network, resulting in the theft and exfiltration of highly-valuable intellectual property.
Similarly, IT once viewed communications solutions like WhatsApp and WeChat as personal apps. Because corporate teams had zero visibility into them, they would not allow employees to do business on them. But in some critical emerging markets, only a small percentage of people use email. Most use mobile chat applications like WhatsApp. It has become a business imperative to use the local technology.
New Security Challenges
These collaboration and communications tools present significant data governance and security challenges for large organizations. In a survey by SafeGuard Cyber:
- 78% of cybersecurity leaders express an inability to protect all communication channels and digital assets6
- 46% say collaboration tools represent the biggest security challenge
- 1 in 3 say their biggest challenge is mobile chat apps, WhatsApp, WeChat, Telegram
- 1 in 5 say their biggest challenge is Video meetings (Zoom, Webex, etc. )
Hybrid work environments will only increase the challenges. As employee devices and laptops move onto the corporate network and then back home where they can be exposed to hackers and more easily infected with malware and ransomware, it will be difficult for security teams to protect employees from threats, detect and respond to insider threats, or stop malware and ransomware.

Only 20% of security professionals feel confident they are effectively mitigating the digital risks from social media, messaging and collaboration apps.
SafeGuardCyber Survey April, 2019
Evolving Threat Landscape
In general, humans are the weakest link in an organizations’ cybersecurity defenses. In 2022, 25% of all breaches were the result of social engineering attacks. When including human error and misuse of privilege, that number jumps to 82% of breaches linked to humans over the past year. According to a recent article in SC Magazine, language-based attacks are now the new normal for business email compromises (BECs) with nearly 75% of attacks using language as the main attack vector. In addition to language, malicious links, weaponized payloads, and common business workflows have become a common proxy to compromise employees and steal money, credentials, or sensitive data. Here are just a few ways bad actors are targeting human nature.
 Social Engineering Threats
Social Engineering Threats
Bad actors use social engineering to trick individuals into sharing sensitive information. Actors use social engineering to exploit basic human nature and often revolve around fear, greed, curiosity, helpfulness, and urgency. Common social engineering attacks include phishing, spear phishing, business email compromise, and impersonation. “According to cloud security company Zscaler, 2021 saw a 29% rise in phishing attacks, driven – it believes, in part – by phishing as a service (PhaaS). Across retail and wholesale, a 400% increase in phishing attacks was observed over the last 12 months, while financial and governmental sectors saw a more-than 100% increase. PhaaS puts pre-built attack tools up for sale in underground marketplaces online, making it easier for non-sophisticated actors to launch successful attacks.”
 Insider Threats
Insider Threats
Insider threats are typically delivered by three types of actors: careless users, malicious insiders, and credential thieves. Careless users inadvertently expose sensitive data by making simple errors or by misconfiguring their defenses. In one common example, healthcare workers email protected healthcare information to the wrong email recipient – a result of address autofill. Malicious insiders intentionally sabotage their employer or steal information for either personal reasons or financial gain. Credential thieves slip through security controls using stolen credentials and go about stealing data or conducting sabotage. While insider threats can be less of a problem than by the activities of external actors, these types of incidents have risen 44% over the past two years, with costs per incident up more than a third to $15.38 million.
 Malware and Ransomware Threats
Malware and Ransomware Threats
Ransomware attacks put critical data at risk of theft or destruction while rendering IT systems inoperable. These attacks are sophisticated forms of malware that are costly to virtually every enterprise, regardless of size or vertical focus. On average, organizations are effectively disabled for 19 days, on average. Ransomware caused at least $8.0 billion in damages in 2018, growing to $11.5 billion in 2019. During 2021, approximately 37% of global organizations were victims of some form of ransomware attack, resulting in $20 billion in damages.
 Multi-Channel Threats
Multi-Channel Threats
As mentioned above, email-based phishing and spear phishing are favorite vectors of attacks and SecOps teams have put in place email security solutions to thwart them. Attackers are adapting their tactics to target users via unprotected social media accounts, mobile chat, and digital collaboration applications. Social media apps like Facebook, collaboration apps such as Microsoft Teams, Slack, and Zoom, and messaging apps like WeChat and Telegram have quickly become embedded in today’s brands and business relationships. These apps allow employees and executives to enter places beyond the usual scope of enterprise data management.
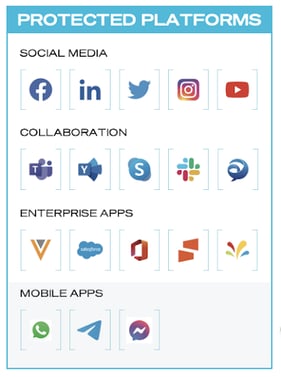
Some of the most popular communications channels used for delivering threats.
Attackers, especially those attempting to commit fraud, impersonation, and business compromise, are evading detection by starting communications in email and then quickly moving conversations to unprotected channels such as Slack or Teams. For this reason, focusing on email is not enough for a comprehensive defense strategy. Security practitioners must provide universal security coverage that determines user identity, behavior analytics, content, and context across all supported communication channels.


Retooling Security with Contextual Analytics
To identify ‘good’ conversations from those representing threats, NLU-based contextual analytics help SOC teams determine the context and intent of communications. Sophisticated ML models use NLU derived context and intent with message metadata to accurately identify threats. This helps security teams take action earlier in the kill chain, before a harmful payload is delivered or credentials are compromised. This approach serves as an added layer of detection that complements existing email security, giving organizations a more proactive threat detection and response capability that can prevent theft and loss before they occur.
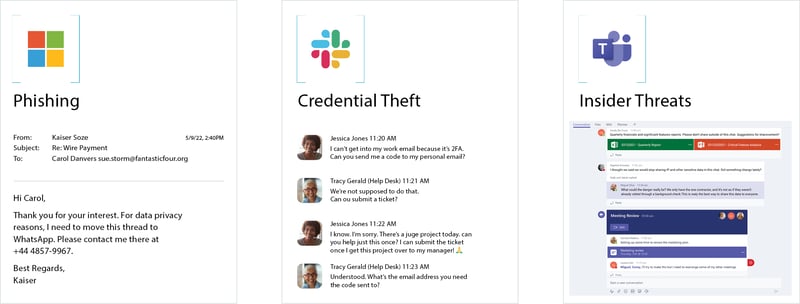
Detected threats include email compromise, fraud (invoice, payment, payroll), insider threat, credential theft, impersonation, and account takeover.

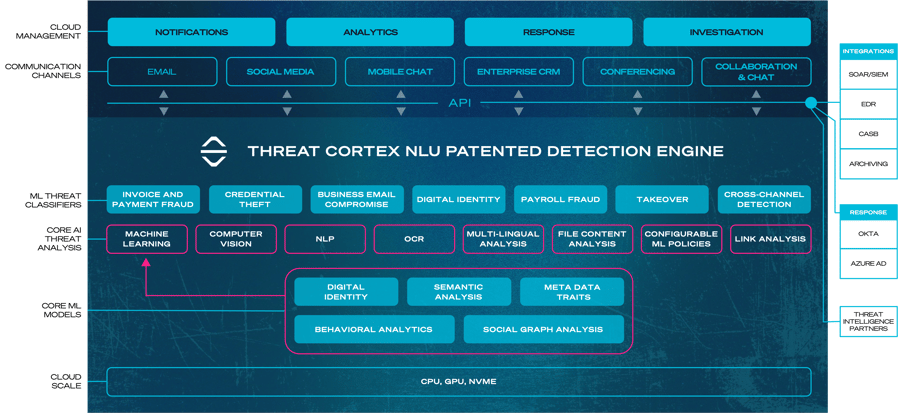
SafeGuard Cyber NLU Platform
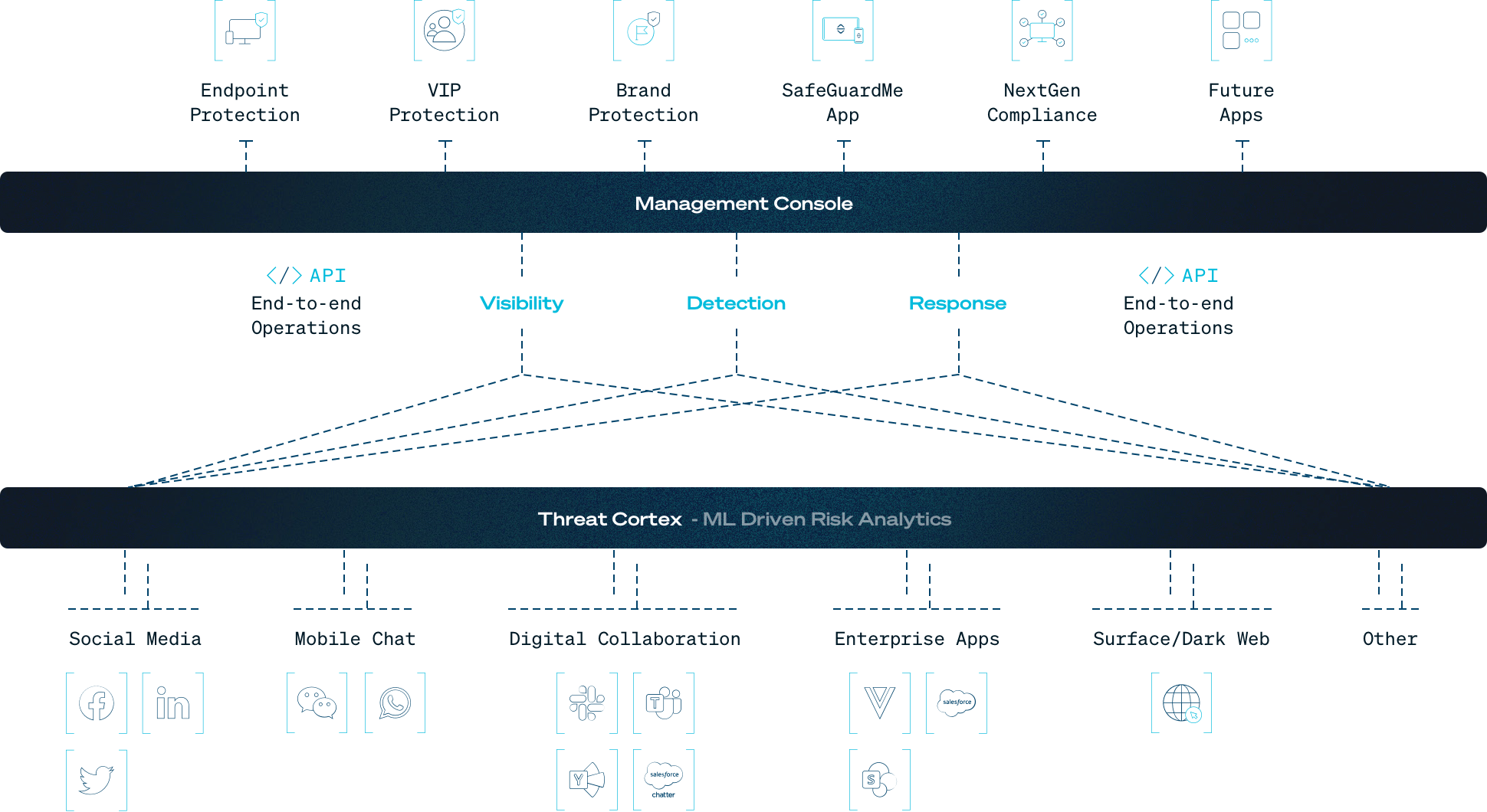
The SafeGuard Cyber platform is a third generation solution that uses NLU and ML to understand the context and intent of human digital communications. It is designed with the SOC in mind, using API integration with communication channels and security infrastructure to make the platform easy to deploy, simple to use, and quick to operationalize.
This patented detection engine accurately identifies social engineering attacks by analyzing a comprehensive set of message features, including:
- Digital Identity - verifying the sender’s identity
- Semantic Analysis - understanding the content of the message
- Metadata Traits - analyzing characteristics of the message
- Behavior Analytics - identifying abnormal behavior
- Social Graph Analysis - analyzing the history of past communication

Detect Threats That Other Solutions Miss
Through a single pane of glass interface, the SafeGuard Cyber platform provides real-time detection and analysis of events within and across workspace channels. Unlike pure behavioral detection solutions, the SafeGuard Cyber platform uses multilingual NLU technology to identify the context and determine intent of communications. While ICES solutions focus on email, SafeGuard Cyber expands the security umbrella to protect 30 other business channels for collaboration, chat, conferencing, social media, and mobile messaging. And unlike CASB solutions that only focus on cloud data protection, SafeGuard Cyber collectively monitors cross-channel activity to detect sophisticated attack campaigns that span multiple channels.

SafeGuardCyber Survey April, 2019
SafeGuardCyber Survey April, 2019
SafeGuardCyber Survey April, 2019
Lorem ipsum dolor
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Nulla urna massa, maximus at neque vel, mollis efficitur.
Benefits
With SafeGuard Cyber’s agentless architecture, organizations benefit from:
Gain unprecedented visibility to respond to internal and external threats in hard-to-see places like direct messages and group channels. Reduce detection and response times in the cloud infrastructure where work gets done.
Be up and running in hours not days. Organizations no longer have to configure agents.
Connect our agentless security platform into your existing cyber defense systems, feeding event data and telemetry into your EDR and SIEM solutions.
Secure Human Connections
Ready to see how SafeGuard Cyber secures modern communication apps wherever they exist?
Expert Insights on Cloud App Risks
Stay up-to-date on the latest insider threats, ransomware, and third-party vulnerabilities.