This time, it’s not only brand impersonation or CEO fraud that they’re leveraging to get what they want. Threat actors are also using a combination of phishing and catfishing techniques to spread malware and steal resources and information.
Let’s delve into the nature of a new campaign – and establish how individuals and organizations can protect themselves with solutions that leverage Natural Language Processing / Understanding (NLP/NLU).
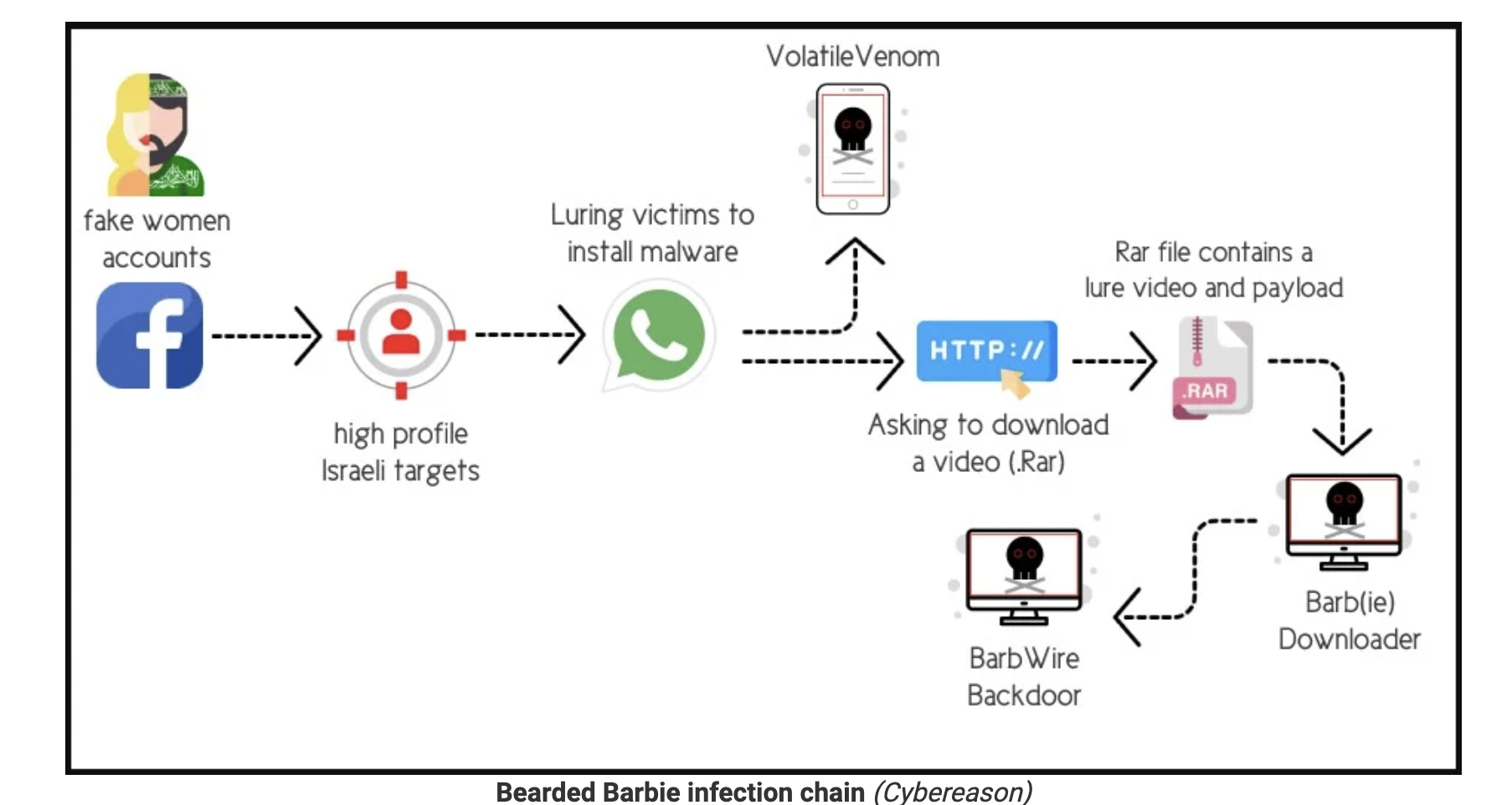
Bearded Barbie: A Marriage of Phishing and Catfishing
Reports of a hacking campaign dubbed as Bearded Barbie were published last month, and it makes use of the expanded risk surface brought on by social media.
APT-C-23, a threat group operating on behalf of Hamas, launched a campaign targeting Israelis working for sensitive industries via Facebook with phishing and catfishing tactics. The group created a fake Facebook profile, usually of a beautiful woman, to initiate conversations with unsuspecting Israeli men. As the hacker earned victims’ trust, the actor then moves the conversation to WhatsApp. From there, the threat actor sends two pieces of malware, one disguised as another chat application, and the other as an explicit video.
These pieces of malware are called VolatileVenom and Barb(ie) Downloader.
- VolatileVenom is an Android implant disguised as a chat application. The attacker convinces the victim to download the app for a more “secure and discreet” communication.
- The explicit video is embedded in a .rar file as the lure. The file also delivers Barb(ie), a downloader component. Barb(ie) downloads and installs BarbWire Backdoor, which fully compromises the victim’s device.
Once the target downloads and installs the applications, threat actors gain the ability to spy on the device, steal a variety of data, and maintain persistence on the infected device.
Two Ways to Defend Against Bearded Barbie Scammers
This sort of phishing attack isn’t the first time that this has happened either. In 2021, Facebook itself revealed that Iranian spies were phishing and catfishing individuals from the US military. The actors disguised themselves as recruiters and promising jobs in a defense contractor or aerospace industries.
Other related instances of sophisticated social engineering techniques used by hackers include posing as scholars to target professors and writers, or as cybersecurity researchers to pull off phishing attacks.
In any case, looking closely at how individuals can defend against these attack styles, we see two primary ways to detect the tactics, techniques, and procedures (TTPs) of this attack:
- File content analysis; and,
- Natural language analysis and detection
File Content Analysis
Non-email messaging platforms traditionally have little to no native malware detection capabilities. Threat actors understand this well. WhatsApp is a frequent vector for sending files without checks, which is why threat actors approach first on social media and then move conversations to WhatsApp.
Many of our customers operating in emerging markets, where WhatsApp is the primary means of business communication, express the concern over lack of visibility into malware.
Natural Language Analysis and Detection
Most spear-phishing attacks leverage some form of social engineering techniques used by hackers to groom targets and earn trust. Cyber espionage campaigns of this order are often long operations to maintain the subterfuge. In this case, the technique is catfishing, with APT-C-23 maintaining the fake Facebook profiles often enough to pass as real. Often, it can be hard to determine whether the messages you receive or the people you correspond to are legitimate.
This is where natural language analysis and detection can help. Natural Language Processing (NLP) and Natural Language Understanding (NLU) can work together to detect social engineering patterns based on the words used, messages context, and intent.
Moreover, effective NLP/NLU solutions use cloud computing power to analyze messages in a language-agnostic way. In this case, even when the language and the text was in Hebrew, a robust NLP/NLU solution will be able to help in detecting language that precedes social engineering techniques used by hackers, without requiring loads of Hebrew training data beforehand. Strong NLU is ready from day one.
Protect Yourself from Social Engineering
We can expect more instances of these phishing and catfishing scams in the future. It is only logical, then, that organizations and individuals start protecting themselves against them by deploying robust cybersecurity solutions that can:
- Proactively monitor, detect, and quarantine malicious files, links, and attachments in social media and mobile chat applications; and,
- Analyze and detect social engineering language and patterns from known and unknown sources.
SafeGuard Cyber’s platform was engineered from the ground up to secure human communications from risks like social engineering. Take the 5-minute tour.
If you are interested in learning more about the SafeGuard Cyber solution, you can take a quick 5-minute tour.