A successful phishing attack can be highly damaging, especially if a user doesn’t have multi-factor authentication enabled or reuses a password for more than one account. But in recent years, the spear-phishing attack – is on the rise.
The entry points for spear-phishing attacks are currently more numerous than ever, because third-party cloud channels have vastly expanded the threat surface. Once, phishing was largely an email problem. But platforms like Microsoft Teams and even WhatsApp have been widely adopted as key enterprise channels, and they are increasingly rivalling company email for the volume and density of communications (a process accelerated by the rise of the remote workforce).However, these cloud channels sit outside the network perimeter, and they present a double-sided problem. First, they offer a new way for employees to be phished (via a WhatsApp message, or a LinkedIn DM), in communications invisible to most security teams. Secondly, these digital channels present a host of new accounts that can be compromised. A bad actor who phishes an employee’s Office 365 credentials can then use those credentials to impersonate that employee on the company’s Team instance.
Common spear phishing examples include, but are not limited to:
- Business email compromise (BEC),
- Whaling,
- CEO fraud,
- Email spoofing, and;
- Fake invoices
With the number of ways threat actors can pull off a successful spear phishing attack, it is both more important and harder than ever for security teams to prevent spear phishing attacks.
Spear Phishing: Phishing Upgraded
Spear phishing attacks are becoming increasingly well-known thanks to an ever-growing list of high-profile spear phishing examples. For example, the richest man in the world was compromised via WhatsApp. In January of 2020, reports emerged describing how Jeff Bezos had been targeted, mostly likely by nation state actors. Bezos was sent a video in a WhatsApp conversation, which he played. However, the video contained malware that penetrated Bezos’s cellphone and exfiltrated a large amount of data within just a few hours. Allegations swirled that the sender of the video was someone Bezos knew: Mohammed bin Salman, the crown prince of Saudi Arabia.
Regardless of the attacker, Bezos suffered a classic spear-phishing attack. Like most people, he had no idea that the link he had been sent was a threat because it came from someone he knew and trusted. A study by BlackHat found that a whopping 66% of social spear-phishing messages were opened by their recipients.
Every month, the perpetrators of spear phishing attacks grow more sophisticated in their methods. According to a Verizon report, in large organization breaches, 50% of attacks involve social phishing. And crucially, these phishing attacks have increasingly expanded into digital communication channels other than email. Nation state actors use social platforms like LinkedIn to make connections and establish trust with multiple targets throughout an organization. Often posing as a job recruiter, they then proceed to send malicious docs to these targets. After the initial compromise, these APT attacks can move laterally to evade and penetrate enterprise defenses.
It’s easy to say that Bezos was careless when he downloaded that video, or to declare that the victims of these APT attacks should pay better attention. But spotting fake and dangerous emails, messages and DMs is very difficult. Relying on individuals’ ability to consistently and accurately distinguish a fraudulent sign-in request from an authentic one is unrealistic.
Guide: Learn how to foil spear phishing attempts
to protect yourself and your company.
Why are Spear Phishing Attacks on the Rise?
Organizations are more and more likely to suffer a spear phishing attack for three key reasons:
1. The adoption of social and collaboration channels
Digital communication channels, like Microsoft Teams, LinkedIn, and even WhatsApp, have supplanted email as the preferred channels for personal and professional communication. By the end of 2021, two out of three businesses are expected to adopt team collaboration apps. Often, the deployment of these channels completely bypasses the traditional enterprise security defense perimeter.
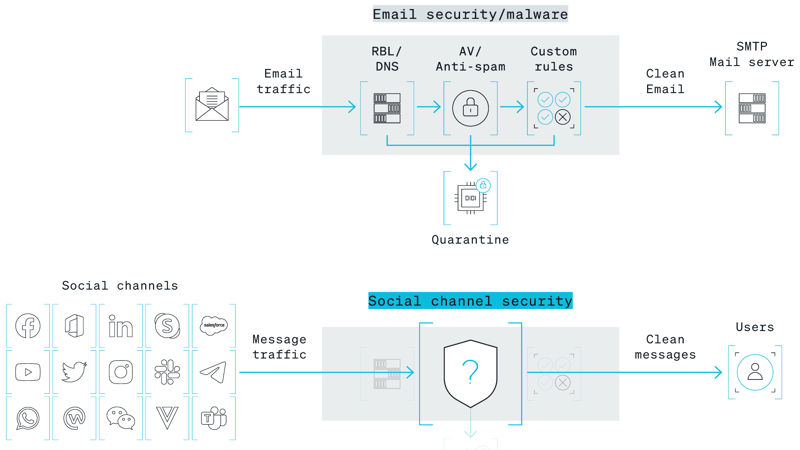
2. The rise and rise of remote workforce and WFH
The COVID-19 pandemic accelerated a trend that was already well underway: the shift of the workforce from enterprise premises to employees’ home offices. According to a Gartner survey, 74% of CFOs intend to shift some employees to remote work permanently. Even if the remote VPN transport is highly secure, home networks are blighted by legacy routers, PCs, and IOT devices. Protecting this highly distributed remote environment from attacks and breaches is a security challenge. In addition, these digital communication channels provide a systematic conduit to user accounts and critical assets, that may be one click away from a data breach via a compromised account.
3. The rise of social cyber attacks
Email security is a $3 billion industry. But security for collaboration, chat, and social channels is nowhere near as well developed. Your average cybersecurity team has few or zero tools that enable proactively prevent spear phishing attacks mounted through LinkedIn, or Slack, or WhatsApp. Bad actors know this, and are shifting their resources to focus on such channels. (This is why more and more of the spear phishing examples that make the news don’t involve email at all.)
How Can Enterprises Protect Their Third-Party Cloud Channels from Spear Phishing Attacks?
All responsible security teams want to know how to stop spear phishing. The key is to meet like with like. A spear phishing attack is likely to arrive via the cloud, so an effective digital risk protection strategy requires comprehensive cloud-based defense, which can stop attacks at the app level to prevent them from moving laterally into endpoints and onto enterprise networks. More specifically, thwarting spear phishers requires:
-
Enhanced Visibility
Security teams need to be able to discover and onboard all authorized accounts for protection, inspect messaging for malicious content, track new connection requests, and archive all account activity. -
Threat Detection
Channels need to be monitored 24/7 for suspicious activity and messaging. All files, attachments and links should be automatically scanned for malware, and connections should be evaluated for known or suspicious bad actors. -
Incident Response
Malware must be quarantined in real time at the app level, and IOC notification details sent to SOC/SIEM for evaluation. Social attacks need to be correlated with EDR.
The spear phishing attack is here to stay. And increasingly, it will become not an email problem, but a Slack problem, a Teams problem, a LinkedIn problem, an Instagram problem. Institute real digital risk protection, and get the visibility and powers you need to protect your enterprise.
Guide: Learn what modern day digital risks are
and how you can combat them with the right protective measures.


