Security and Compliance for Tech Industry
Cloud-based apps are often the point of origination for today's social engineering and cybersecurity threats. These apps are vital to innovation and growth teams. Secure the business communications that drive revenue.
We're Here to Help
Protect your organizations from regulatory risks in digital communications. Get in touch with our solutions architects!

Talk to an Expert
of enterprise IT and security professionals citing that unsanctioned apps are their biggest security and compliance concerns
of enterprise and IT and security professionals cite data loss as their biggest cyber safety concerns
of breaches into large organizations were the result of social phishing
Source: Verizon Data Breach Report
Dedicated SaaS solution for end-to-end digital risk protection
.png
)
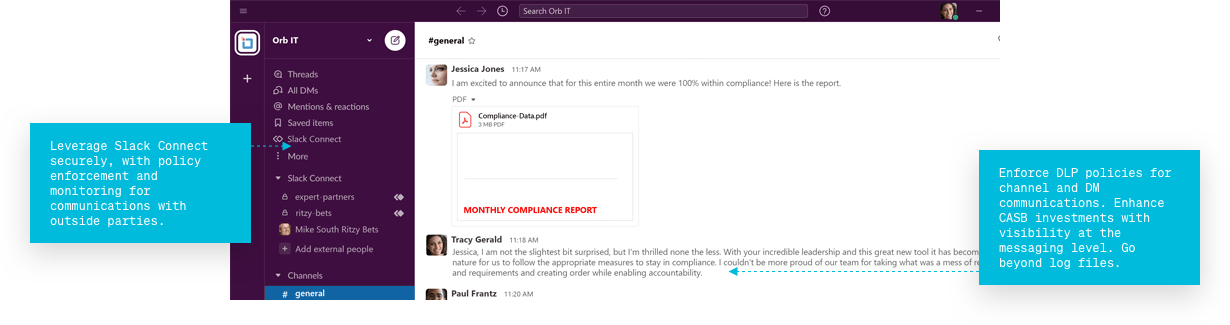
Enforce DLP policies for
Channel and DM communications. Enhance CASB investments with visibility at the messaging level. Go beyond log files.
Leverage Slack or Teams
Connect securely, with policy enforcement and monitoring for communications with outside parties.
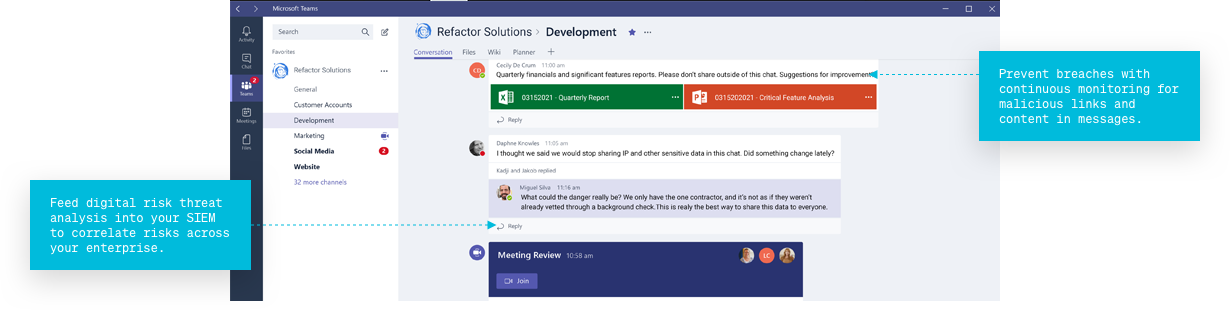

Prevent breaches
With continuous monitoring for malicious links and content in messages.
Feed digital risk
Threat analysis into your SIEM to correlate risks across your enterprise.
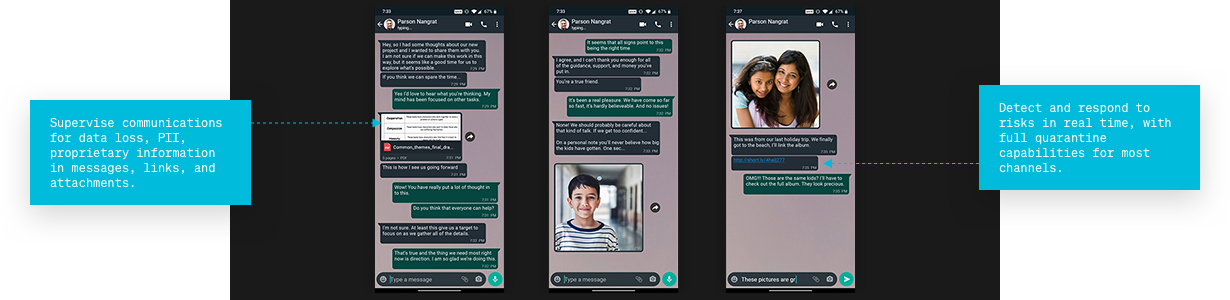

Supervise communications
For data loss, PII, proprietary information in messages, links, and attachments.
Detect and respond
To risks in real time, with full quarantine capabilities for most channels.
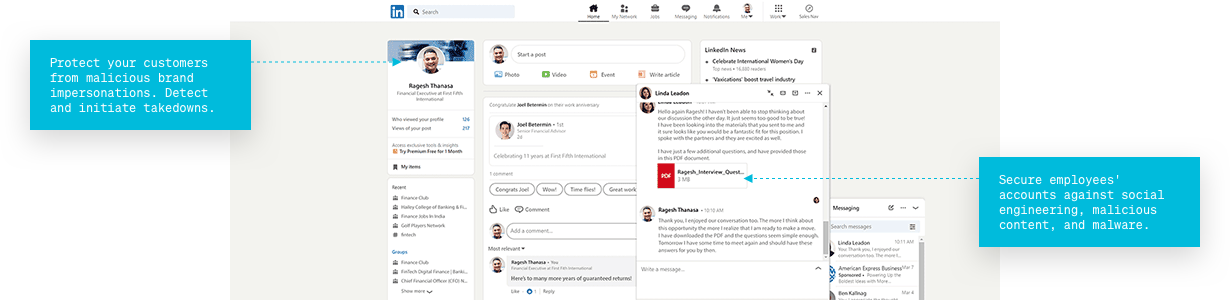

Protect your customers from malicious brand impersonations
detect and initiate takedowns.
Secure employees' accounts
against social engineering, malicious content, and malware.
See How Customers Protect Human Connections
"Our company is growing rapidly, and that means our risk exposure has too. SafeGuard Cyber is a vital partner in securing the many business communications platforms we need to continue growing and serving our clients to the highest standard."

"SafeGuard Cyber has streamlined our social media information security and governance. This outcome supports the growing use of modern communication platforms without the added operational overhead."
"With the newfound power to ensure compliance, wealth managers are able to securely and compliantly meet their customers where they are."
Secure Communication and Collaboration to Drive Growth
Security and Compliance
You set the rules and we do the rest. Gain detection and response capabilities to mitigate risks including data loss, malware, and compliance violations.
Secure Digital Transformation
Use new technology to engage with customers wherever they communicate. Gain business agility with seamless security and rapid time to value.
Protect Your Brand
Prevent brand fraud and impersonation on your cloud applications. Protect your executives and employees from attacks that can compromise your organization.
Ready to Get Started?
Ready to see how SafeGuard Cyber secures modern communication apps wherever they exist?
Expert Insights on Cloud App Risks
Stay up-to-date on the latest social engineering, insider threats, and ransomware vulnerabilities.








