Secure Collaboration and Communication Apps
Business communications are spilling out of secure email into unprotected apps. Security teams have blind spots to the human threat vector. Last year, 85% of breaches involved this vector, compared to vulnerability exploits (3%). Learn how to effectively allocate resources to stop advanced social engineering and targeted threats to your workforce.
We're Here to Help
Secure your organization from risks in cloud communications. Get in touch with our solutions architects!

Secure Collaboration Apps
Collaboration platforms like Microsoft Teams, Slack, and Zoom provide business agility and fuel faster innovation. Secure the accounts, assets, and communications in these critical cloud apps, just as you would email.
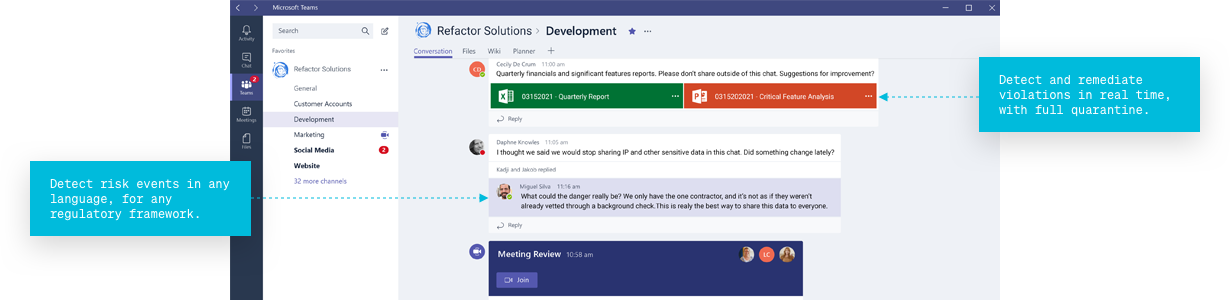

Detect risk events
in any language, for any regulatory framework.
Detect and remediate violations
in real time, with full quarantine.
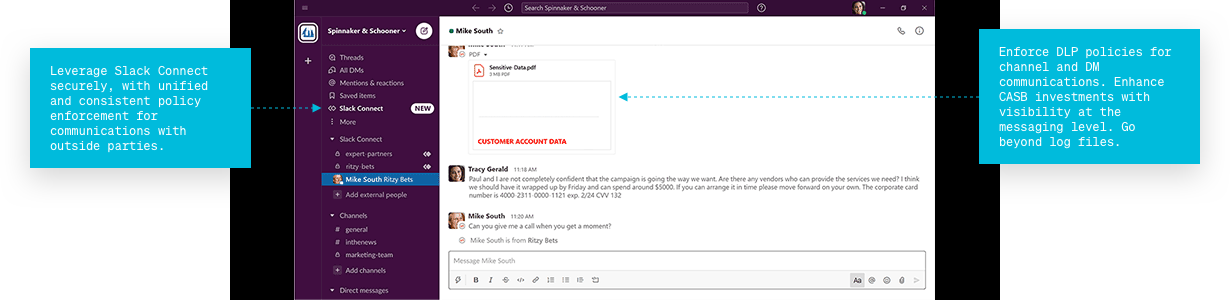

Enforce
DLP policies for channel and DM communications. Enhance CASB investments with visibility at the messaging level. Go beyond log files.
Leverage
Slack or Teams Connect securely, with policy enforcement and monitoring for communications with outside parties.
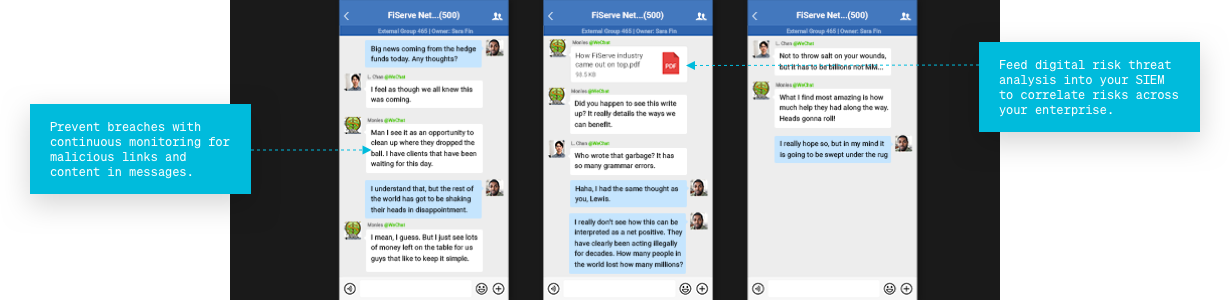

Prevent
Breaches with continuous monitoring for malicious links and content in messages.
Feed
Digital risk threat analysis into your SIEM to correlate risks across your enterprise.
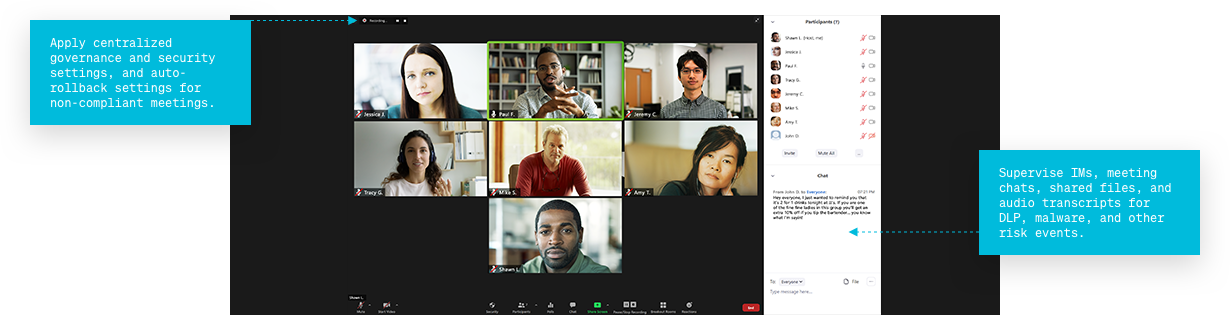

Supervise
IMs, meeting chats, shared files, and audio transcripts for DLP, malware, and other risk events.
Apply
Centralized governance and security settings, and auto-rollback settings for non-compliant meetings.
of companies stating that they now view team collaboration as a primary means of getting work done
Source: SafeGuard Cyber x Metrigy Report
of security leaders view the biggest security and compliance challenge is the use of unsanctioned apps
of successful companies have proactive collaboration security plans
Source: SafeGuard Cyber x Metrigy Report
How It Works
Agentless Architecture
Portable security layer is extended to any instance for no-hassle, agentless onboarding.
API Integrations
Full communication context and intent through API native integrations.
Detection and Response
Single pane of glass to prevent lateral movement and propagation of attacks.
Secure Human Connections
Ready to see how SafeGuard Cyber secures modern communication apps wherever they exist?
Expert Insights on Cloud App Risks
Stay up-to-date on the latest social engineering, insider threats, and ransomware vulnerabilities.






