Contextual AI for Multi-Channel Business Communications
SafeGuard Cyber provides security and compliance for your business communications. Stop Credential Theft, Phishing, BEC, Social Engineering, Insider Threats, and Policy violations across the communication channels used by today's modern enterprise.
of Business Communication takes place outside of email
of cyberattacks leveraged identity-based techniques to compromise legitimate credentials
average cost of most expensive attacks are initiated by malicious insiders
Prevent multi-channel attacks across your
critical business communications

The only platform on the market to provide unified visibility across the entire communications attack surface, eliminating visibility gaps and saving security and compliance teams time and money by replacing siloed solutions.
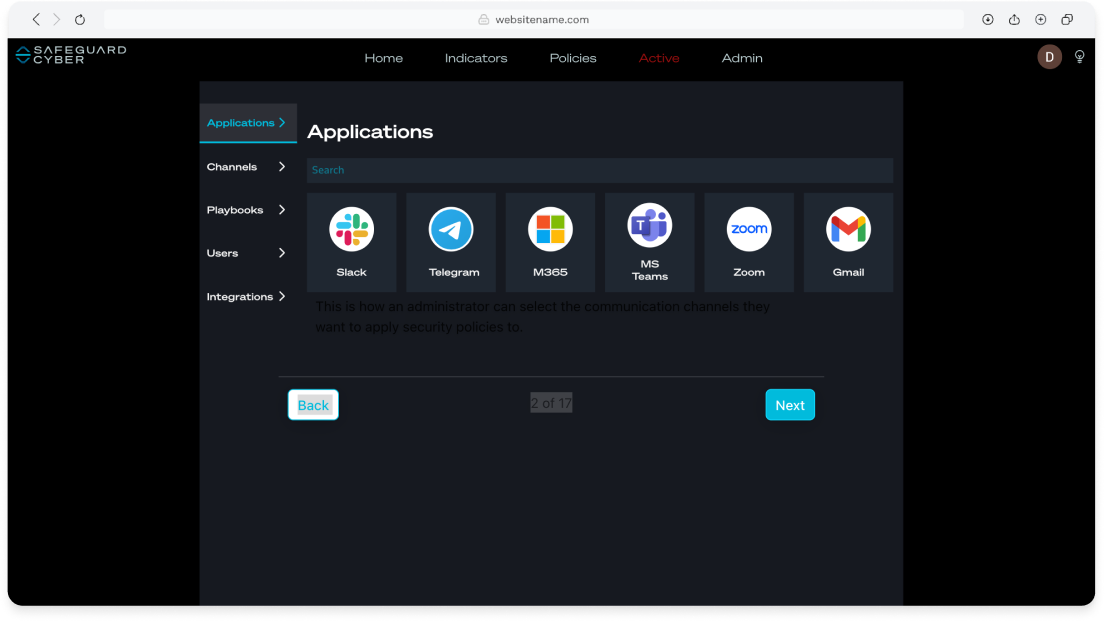
With deep visibility into business communication channels – from Microsoft 365 email to Slack, Teams, Zoom, Telegram, and WhatsApp – security teams can detect and investigate risks in a centralized view.
.png?width=589&height=422&name=Group%20178%20(1).png)
The FirstSight platform is built on an ontological architecture that utilizes LLMs, behavioral analysis, social knowledge graphs, and generative AI, FirstSight incorporates domain-specific knowledge about the customer's enterprise.
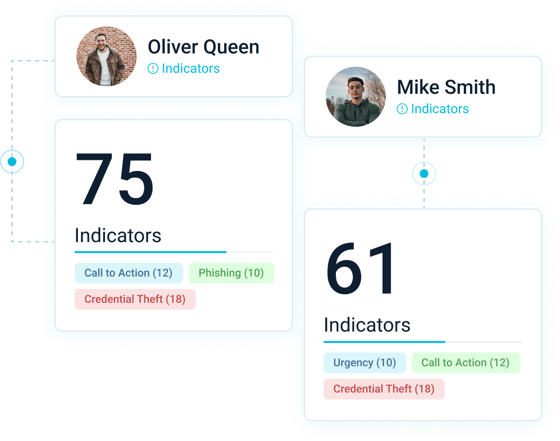
Enables resource-constrained organizations to effectively prioritize remediation of the biggest risks to an organization, ensuring the safety, integrity, and compliance of worldwide business communications.

The only platform on the market to provide unified visibility across the entire communications attack surface, eliminating visibility gaps and saving security and compliance teams time and money by replacing siloed solutions.
With deep visibility into business communication channels – from Microsoft 365 email to Slack, Teams, Zoom, Telegram, and WhatsApp – security teams can detect and investigate risks in a centralized view.
.png?width=589&height=422&name=Group%20178%20(1).png)
The FirstSight platform is built on an ontological architecture that utilizes LLMs, behavioral analysis, social knowledge graphs, and generative AI, FirstSight incorporates domain-specific knowledge about the customer's enterprise.

Enables resource-constrained organizations to effectively prioritize remediation of the biggest risks to an organization, ensuring the safety, integrity, and compliance of worldwide business communications.
Stop high-frequency and costly attacks
insider risk
Insiders often pose a bigger threat to organizations than outsiders. Whether it’s accidental or intentional, insiders can cause millions of dollars worth of damage.
Business compromise
Attackers are tailoring their attack mechanisms for well-known cloud workplace channels like Slack, Salesforce, LinkedIn, Zoom, WhatsApp, Telegram, and many more
insider risk
Insiders often pose a bigger threat to organizations than outsiders. Whether it’s accidental or intentional, insiders can cause millions of dollars worth of damage.
The FirstSight Platform
FirstSight is a next-generation cybersecurity platform, powered by contextual AI, that empowers security teams investigate and remediate unmonitored communications in minutes.
By analyzing language and behavior across all communication channels, FirstSight alerts security teams to high frequency and costly attacks such as credential theft, impersonation, phishing, malware, policy violations, and insider threats across the expanding communication attack surface.
Why customers trust SafeGuard Cyber

.png)















Secure Human Connections
Ready to see how SafeGuard Cyber secures
modern communication apps wherever they exist?
Get a live platform demo
We’ll work with you to better understand your business and recommend a solution to solve your security needs.
Talk to a communication risk expert
We're here to guide as you consider adopting new cloud communication apps.
Expert Insights on Cloud App Risks
Stay up-to-date on regulatory compliance risks that occur in collaboration, mobile chat, conferencing, social media, and email.
By subscribing you agree to receive the SafeGuard Cyber newsletter and other communications from SafeGuard Cyber news, services, and events. I have read the Privacy Policy and agree to it.








